Enhancing Security in Internet of Healthcare Application using Secure Convolutional Neural Network
Main Article Content
Abstract
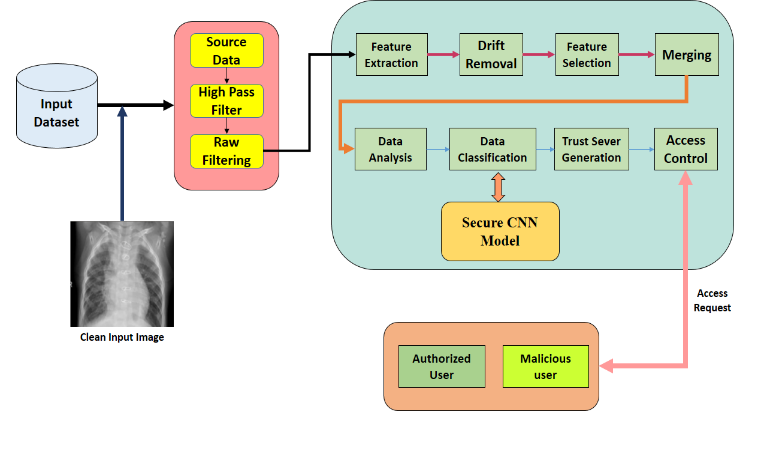
The ubiquity of Internet of Things (IoT) devices has completely changed the healthcare industry by presenting previously unheard-of potential for remote patient monitoring and individualized care. In this regard, we suggest a unique method that makes use of Secure Convolutional Neural Networks (SCNNs) to improve security in Internet-of-Healthcare (IoH) applications. IoT-enabled healthcare has advanced as a result of the integration of IoT technologies, giving it impressive data processing powers and large data storage capacity. This synergy has led to the development of an intelligent healthcare system that is intended to remotely monitor a patient's medical well-being via a wearable device as a result of the ongoing advancement of the Industrial Internet of Things (IIoT). This paper focuses on safeguarding user privacy and easing data analysis. Sensitive data is carefully separated from user-generated data before being gathered. Convolutional neural network (CNN) technology is used to analyse health-related data thoroughly in the cloud while scrupulously protecting the privacy of the consumers.The paper provide a secure access control module that functions using user attributes within the IoT-Healthcare system to strengthen security. This module strengthens the system's overall security and privacy by ensuring that only authorised personnel may access and interact with the sensitive health data. The IoT-enabled healthcare system gets the capacity to offer seamless remote monitoring while ensuring the confidentiality and integrity of user information thanks to this integrated architecture.
Article Details
References
O. Keskes and R. Noumeir, “Vision-based fall detection using st-gcn,” IEEE Access, vol. 9, pp. 28224–28236, 2021.
J. de Batlle, M. Massip, E. Vargiu et al., “Implementing mobile health–enabled integrated care for complex chronic patients: intervention effectiveness and cost-effectiveness study,” JMIR mHealth and uHealth, vol. 9, no. 1, article e22135, 2021.
H. Bolhasani, M. Mohseni, and A. M. Rahmani, “Deep learning applications for IoT in health care: a systematic review,” Informatics in Medicine Unlocked, vol. 23, article 100550, 2021.
Y. Yang, X. Liu, and R. H. Deng, “Lightweight break-glass access control system for healthcare Internet-of-Things,” IEEE Transactions on Industrial Informatics, vol. 14, no. 8, pp. 3610–3617, 2018.
J. Liu, H. Tang, R. Sun, X. Du, and M. Guizani, “Lightweight and privacy-preserving medical services access for healthcare cloud,” IEEE Access, vol. 7, pp. 106951–106961, 2019.
S. Roy, A. K. Das, S. Chatterjee, N. Kumar, S. Chattopadhyay, and J. J. P. C. Rodrigues, “Provably secure fine-grained data access control over multiple cloud servers in mobile cloud computing based healthcare applications,” IEEE Transactions on Industrial Informatics, vol. 15, no. 1, pp. 457–468, 2019.
S. Ajani and M. Wanjari, "An Efficient Approach for Clustering Uncertain Data Mining Based on Hash Indexing and Voronoi Clustering," 2013 5th International Conference and Computational Intelligence and Communication Networks, 2013, pp. 486-490, doi: 10.1109/CICN.2013.106.
B. Jang, and J. W. Kim, “Collaborative Ehealth privacy and security: an access control with attribute revocation based on OBDD access structure,” IEEE Journal of Biomedical and Health Informatics, vol. 24, no. 10, pp. 2960–2972, 2020.
J. Sun, H. Xiong, X. Liu, Y. Zhang, X. Nie, and R. H. Deng, “Lightweight and privacy-aware fine-grained access control for IoT-oriented smart health,” IEEE Internet of Things Journal, vol. 7, no. 7, pp. 6566–6575, 2020.
K. Fan, Q. Pan, K. Zhang et al., “A secure and verifiable data sharing scheme based on blockchain in vehicular social networks,” IEEE Transactions on Vehicular Technology, vol. 69, no. 6, pp. 5826–5835, 2020.
F. Al-Turjman and B. Deebak, “Privacy-aware energy-efficient frame-work using the Internet of Medical Things for COVID-19,” IEEE Internet of Things Magazine, vol. 3, no. 3, pp. 64–68, 2020.
M. Shariq, K. Singh, M. Y. Bajuri, A. A. Pantelous, A. Ahmadian, and M. Salimi, “A secure and reliable RFID authentication protocol using digital schnorr cryptosystem for IoT-enabled healthcare in COVID-19 scenario,” Sustainable Cities and Society, vol. 75, article 103354, 2021.
G. S. Gunanidhi, “Extensive analysis of Internet of Things based health care surveillance system using Rfid assisted lightweight cryptographic methodology,” Turkish Journal of Computer and Mathematics Education (TURCOMAT), vol. 12, no. 10, pp. 6391–6398, 2021.
P. Gope, A. K. Das, N. Kumar, and Y. Cheng, ‘‘Lightweight and physically secure anonymous mutual authentication protocol for real-time data access in industrial wireless sensor networks,’’ IEEE Trans. Ind. Informat., vol. 15, no. 9, pp. 4957–4968, Sep. 2019.
H. Yeh, T. Chen, P. Liu, T. Kim, and H. Wei, ‘‘A secured authentication protocol for wireless sensor networks using elliptic curves cryptography,’’ Sensors, vol. 11, no. 5, pp. 4767–4779, May 2011
Khetani, V. ., Gandhi, Y. ., Bhattacharya, S. ., Ajani, S. N. ., & Limkar, S. . (2023). Cross-Domain Analysis of ML and DL: Evaluating their Impact in Diverse Domains. International Journal of Intelligent Systems and Applications in Engineering, 11(7s), 253–262. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2951
A. Agarwal, R. Singh, M. Vatsa, and N. Ratha, ‘‘Are image-agnostic universal adversarial perturbations for face recognition difficult to detect?’’ in Proc. IEEE 9th Int. Conf. Biometrics Theory, Appl. Syst. (BTAS), Oct. 2018, pp. 1–7
Z. Yahya, M. Hassan, S. Younis, and M. Shafique, ‘‘Probabilistic analysis of targeted attacks using transform-domain adversarial examples,’’ IEEE Access, vol. 8, pp. 33855–33869, 2020.
W. Zhang, ‘‘Generating adversarial examples in one shot with imageto-image translation GAN,’’ IEEE Access, vol. 7, pp. 151103–151119, 2019.
J. Jia, A. Salem, M. Backes, Y. Zhang, and N. Z. Gong, ‘‘MemGuard: Defending against black-box membership inference attacks via adversarial examples,’’ in Proc. ACM SIGSAC Conf. Comput. Commun. Secur., Nov. 2019, pp. 259–274.
A. Goel, A. Agarwal, M. Vatsa, R. Singh, and N. Ratha, ‘‘Securing CNN model and biometric template using blockchain,’’ in Proc. IEEE 10th Int. Conf. Biometrics Theory, Appl. Syst. (BTAS), Sep. 2019, pp. 1–7
Z. Xu, F. Yu, and X. Chen, ‘‘LanCe: A comprehensive and lightweight CNN defense methodology against physical adversarial attacks on embedded multimedia applications,’’ in Proc. 25th Asia South Pacific Design Autom. Conf. (ASP-DAC), Jan. 2020, pp. 470–475.
] A. Simonet-Boulogne, A. Solberg, A. Sinaeepourfard, D. Roman, F. Perales, G. Ledakis, I. Plakas, and S. Sengupta, ‘‘Toward blockchainbased fog and edge computing for privacy-preserving smart cities,’’ Frontiers Sustain. Cities, vol. 4, p. 136, Sep. 2022
A. Kurakin, I. J. Goodfellow, and S. Bengio, ‘‘Adversarial examples in the physical world,’’ in Artificial Intelligence Safety and Security. London, U.K.: Chapman & Hall/CRC, 2018, pp. 99–112.
X. Yuan, P. He, Q. Zhu, and X. Li, ‘‘Adversarial examples: Attacks and defenses for deep learning,’’ IEEE Trans. Neural Netw. Learn. Syst., vol. 30, no. 9, pp. 2805–2824, Sep. 2019.
U. Shaham, Y. Yamada, and S. Negahban, ‘‘Understanding adversarial training: Increasing local stability of supervised models through robust optimization,’’ Neurocomputing, vol. 307, pp. 195–204, Sep. 2018.
H. Shu, R. Shi, Q. Jia, H. Zhu, and Z. Chen, ‘‘MFI-PSO: A flexible and effective method in adversarial image generation for deep neural networks,’’ 2020, arXiv:2006.03243
G. Goswami, A. Agarwal, N. Ratha, R. Singh, and M. Vatsa, ‘‘Detecting and mitigating adversarial perturbations for robust face recognition,’’ Int. J. Comput. Vis., vol. 127, nos. 6–7, pp. 719–742, 2019
A. Agarwal, R. Singh, M. Vatsa, and N. Ratha, ‘‘Are image-agnostic universal adversarial perturbations for face recognition difficult to detect?’’ in Proc. IEEE 9th Int. Conf. Biometrics Theory, Appl. Syst. (BTAS), Oct. 2018, pp. 1–7
K. Kansal, P. S. Krishna, P. B. Jain, S. R, P. Honnavalli, and S. Eswaran, ‘‘Defending against adversarial attacks on COVID-19 classifier: A denoiser-based approach,’’ Heliyon, vol. 8, no. 10, Oct. 2022, Art. no. e11209.
X. Ma, Y. Niu, L. Gu, Y. Wang, Y. Zhao, J. Bailey, and F. Lu, ‘‘Understanding adversarial attacks on deep learning based medical image analysis systems,’’ Pattern Recognit., vol. 110, Feb. 2021, Art. no. 107332.
Z. Yahya, M. Hassan, S. Younis, and M. Shafique, ‘‘Probabilistic analysis of targeted attacks using transform-domain adversarial examples,’’ IEEE Access, vol. 8, pp. 33855–33869, 2020.
W. Zhang, ‘‘Generating adversarial examples in one shot with imageto-image translation GAN,’’ IEEE Access, vol. 7, pp. 151103–151119, 2019.
M. Nassar, K. Salah, M. H. urRehman, and D. Svetinovic, ‘‘Blockchain for explainable and trustworthy artificial intelligence,’’ WIREs Data Mining Knowl. Discovery, vol. 10, no. 1, Jan. 2020, Art. no. e1340.
Z. Xu, F. Yu, and X. Chen, ‘‘LanCe: A comprehensive and lightweight CNN defense methodology against physical adversarial attacks on embedded multimedia applications,’’ in Proc. 25th Asia South Pacific Design Autom. Conf. (ASP-DAC), Jan. 2020, pp. 470–475
J. Jia, A. Salem, M. Backes, Y. Zhang, and N. Z. Gong, ‘‘MemGuard: Defending against black-box membership inference attacks via adversarial examples,’’ in Proc. ACM SIGSAC Conf. Comput. Commun. Secur., Nov. 2019, pp. 259–274
Chest X Ray Dataset: https://www.kaggle.com/datasets/paultimothymooney/chest-xray-pneumonia