Enhancing Confidentiality and Privacy Preservation in e-Health to Enhanced Security
Main Article Content
Abstract
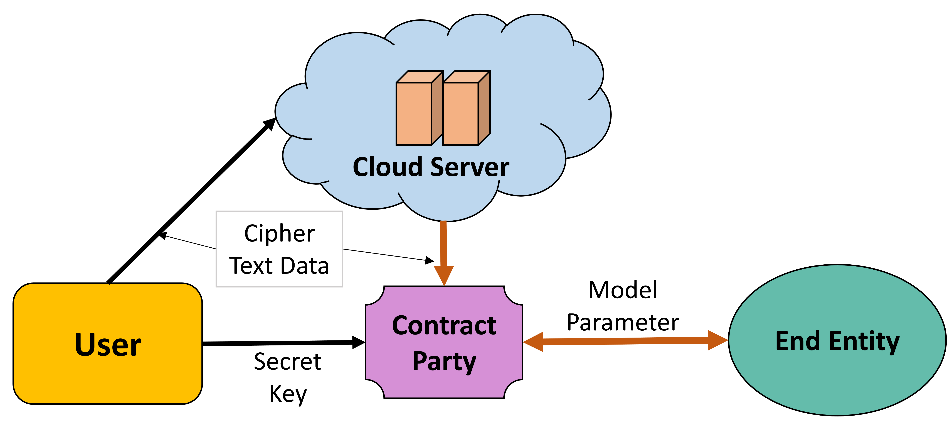
Electronic health (e-health) system use is growing, which has improved healthcare services significantly but has created questions about the privacy and security of sensitive medical data. This research suggests a novel strategy to overcome these difficulties and strengthen the security of e-health systems while maintaining the privacy and confidentiality of patient data by utilising machine learning techniques. The security layers of e-health systems are strengthened by the comprehensive framework we propose in this paper, which incorporates cutting-edge machine learning algorithms. The suggested framework includes data encryption, access control, and anomaly detection as its three main elements. First, to prevent unauthorised access during transmission and storage, patient data is secured using cutting-edge encryption technologies. Second, to make sure that only authorised staff can access sensitive medical records, access control mechanisms are strengthened using machine learning models that examine user behaviour patterns. This research's inclusion of machine learning-based anomaly detection is its most inventive feature. The technology may identify variations from typical data access and usage patterns, thereby quickly spotting potential security breaches or unauthorised activity, by training models on past e-health data. This proactive strategy improves the system's capacity to successfully address new threats. Extensive experiments were carried out employing a broad dataset made up of real-world e-health scenarios to verify the efficacy of the suggested approach. The findings showed a marked improvement in the protection of confidentiality and privacy, along with a considerable decline in security breaches and unauthorised access events.
Article Details
References
Y. Chen, Z. Lu, H. Xiong, and W. Xu, “Privacy-preserving data aggregation protocol for fog computing-assisted vehicle-to-infrastructure scenario,” Security and Communication Networks, vol. 2018, pp. 1–14, 2018.
L. Yang, W. Zou, and J. Wang, “EdgeShare: a blockchain-based edge data-sharing framework for industrial Internet of things,” vol. 43, 2021.
F. Chen, J. Huang, C. Wang et al., “Data access control based on blockchain in medical cyber physical systems,” Security and Communication Networks, vol. 34, pp. 1–14, 2021.
K. Gu, W. Jia, G. Wang, and S. Wen, “Efficient and secure attribute-based signature for monotone predicates,” ActaInformatica, vol. 54, no. 5, pp. 521–541, 2017.
H.. Wang and Y.. Song, “Secure cloud-based EHR system using attribute-based cryptosystem and blockchain,” Journal of Medical Systems, vol. 42, no. 8, pp. 152–164, 2018.
S. Ajani and M. Wanjari, "An Efficient Approach for Clustering Uncertain Data Mining Based on Hash Indexing and Voronoi Clustering," 2013 5th International Conference and Computational Intelligence and Communication Networks, 2013, pp. 486-490, doi: 10.1109/CICN.2013.106.
Khetani, V., Gandhi, Y., Bhattacharya, S., Ajani, S. N., & Limkar, S. (2023). Cross-Domain Analysis of ML and DL: Evaluating their Impact in Diverse Domains. International Journal of Intelligent Systems and Applications in Engineering, 11(7s), 253–262. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2951
R..Guo, H.. Shi, Q. Zhao, and D. Zheng, “Secure attribute-based signature scheme with multiple authorities for blockchain in electronic health records systems,” IEEE Access, vol. 6, pp. 11676–11686, 2018.
J. S. Lee, C. J. Chew, and J. Y. Liu, “Medical blockchain: data sharing and privacy preserving of EHR based on smart contract,” vol. 74.
R. Zou, X. Lv, and J. Zhao, “SPChain: blockchain-based medical data sharing and privacy-preserving eHealth system,” Information Processing & Management, vol. 58, no. 4, Article ID 102604, 2021.
Z. Chen, W. Xu, B. Wang, and H. Yu, “A blockchain-based preserving and sharing system for medical data privacy,” Future Generation Computer Systems, vol. 124, pp. 338–350, 2021.
A. Kosba, A. Miller, and E. Shi, “Hawk: the blockchain model of cryptography and privacy-preserving smart contracts,” in Proceedings of the 2016 IEEE Symposium on Security and Privacy, pp. 839–858, IEEE Press, Los Alamitos, CA, USA, 2016.
P. Golle, K. Leytonbrown, and I. Mironov, “Incentives for sharing in peer-to-peer networks,” Lecture Notes in Computer Science, vol. 49, pp. 75–87, 2001.
Y. Lu, X. Huang, Y. Dai, S. Maharjan, and Y. Zhang, “Blockchain and federated learning for privacy-preserved data sharing in industrial IoT,” IEEE Transactions on Industrial Informatics, vol. 16, no. 6, pp. 4177–4186, 2020.
X. Huang, Y. Lu, K. Zhang, S. Maharjan, and Y. Zhang, “Blockchain empowered asynchronous federated learning for secure data sharing in Internet of vehicles,” IEEE Transactions on Vehicular Technology, vol. 69, no. 4, pp. 4298–4311, 2020.
A. A. Shrier, A. Chang, and N. Diakun-Thibault, Blockchain and Health IT: Algorithms, Privacy, and Data, 2016.
X. Yue, H. Wang, D. Jin, M. Li, and W. Jiang, “Healthcare data gateways: found healthcare intelligence on blockchain with novel privacy risk control,” Journal of Medical Systems, vol. 40, no. 10, p. 218, 2016.
H. Li Hao, G. Xu, S. Liu, and H. Yang, “Towards efficient and privacy-preserving federated deep learning,” in Proceedings of the ICC 2019 - 2019 IEEE International Conference on Communications, pp. 1–6, ICC), Shanghai, China, May 2019.
C. Priebe, K. Vaswani, and M. Costa, “EnclaveDB: A Secure Database Using SGX,” in Proceedings of the 2018 IEEE Symposium on Security and Privacy (SP), IEEE, San Francisco, CA, USA, May 2018.
R. Kunkel, D. L. Quoc, and F. Gregor, “TensorSCONE: a secure TensorFlow framework using intel SGX,” vol. 42, 2019.
M. Abadi, P. Barham, and J. Chen, “TensorFlow: a system for large-scale machine learning,” USENIX Association, vol. 12, 2016.
Q. Miao, H. Lin, J. Hu, and X. Wang, “An intelligent and privacy-enhanced data sharing strategy for blockchain-empowered Internet of Things,” Digital Communications and Networks, vol. 88, 2022.
Kruse, C.S.; Mileski, M.; Vijaykumar, A.G.; Viswanathan, S.V.; Suskandla, U.; Chidambaram, Y. Impact of electronic health records on long-term care facilities: Systematic review. JMIR Med. Inform. IEEE 2017, 5, e35.
Butpheng, C.; Yeh, K.-H.; Xiong, H. Security and Privacy in IoT-Cloud-Based e-Health Systems—A Comprehensive Review. Symmetry 2020, 12, 1191.
Ismail, L.; Materwala, H. Blockchain Paradigm for Healthcare: Performance Evaluation. Symmetry 2020, 12, 1200.
Malluhi, Q.; Tran, V.D.; Trinh, V.C. Decentralized Broadcast Encryption Schemes with Constant Size Ciphertext and Fast Decryption. Symmetry 2020, 12, 969.
Hassen, O.A.; Abdulhussein, A.A.; Darwish, S.M.; Othman, Z.A.; Tiun, S.; Lotfy, Y.A. Towards a Secure Signature Scheme Based on Multimodal Biometric Technology: Application for IOT Blockchain Network. Symmetry 2020, 12, 1699.
Abdulghani, H.A.; Nijdam, N.A.; Collen, A.; Konstantas, D. A Study on Security and Privacy Guidelines, Countermeasures, Threats: IoT Data at Rest Perspective. Symmetry 2019, 11, 774.
Huh, J.-H. Big Data Analysis for Personalized Health Activities: Machine Learning Processing for Automatic Keyword Extraction Approach. Symmetry 2018, 10, 93. Kang, J.; Chung, H.; Lee, J.; Park, J.H. The Design and Analysis of a Secure Personal Healthcare System Based on Certificates. Symmetry 2016, 8, 129.
Griebel, L.; Prokosch, H.-U.; Köpcke, F.; Toddenroth, D.; Christoph, J.; Leb, I.; Engel, I.; Sedlmayr, M. A scoping review of cloud computing in healthcare. BMC Med. Inform. Decis. Making 2015, 15, 17.
Ven?kauskas, A.; Štuikys, V.; Toldinas, J.; Jusas, N. A Model-Driven Framework to Develop Personalized Health Monitoring. Symmetry 2016, 8, 65.
Chenthara, S.; Ahmed, K.; Wang, H.; Whittaker, F. Security and Privacy-Preserving Challenges of e-Health Solutions in Cloud Computing. IEEE Access 2019, 7, 74361–74382.
Razaque, A.; Amsaad, F.; Khan, M.J.; Hariri, S.; Chen, S.; Siting, C.; Ji, X. Survey: Cybersecurity Vulnerabilities, Attacks and Solutions in the Medical Domain. IEEE Access 2019, 7, 168774–168797.
Kim, J.W.; Edemacu, K.; Jang, B. MPPDS: Multilevel Privacy-Preserving Data Sharing in a Collaborative eHealth System. IEEE Access 2019, 7, 109910–109923.
Bouras, M.A.; Lu, Q.; Zhang, F.; Wan, Y.; Zhang, T.; Ning, H. Distributed Ledger Technology for eHealth Identity Privacy: State of The Art and Future Perspective. Sensors 2020, 20, 483.
Thatikonda, R., Padthe, A., Vaddadi, S. A., & Arnepalli, P. R. R. (2023). Effective Secure Data Agreement Approach-based cloud storage for a healthcare organization. International Journal of Smart Sensor and Adhoc Network, 60-70.
Thatikonda, R., Vaddadi, S.A., Arnepalli, P.R.R. et al. Securing biomedical databases based on fuzzy method through blockchain technology. Soft Comput (2023). https://doi.org/10.1007/s00500-023-08355-x