Adversarial Sample Generation using the Euclidean Jacobian-based Saliency Map Attack (EJSMA) and Classification for IEEE 802.11 using the Deep Deterministic Policy Gradient (DDPG)
Main Article Content
Abstract
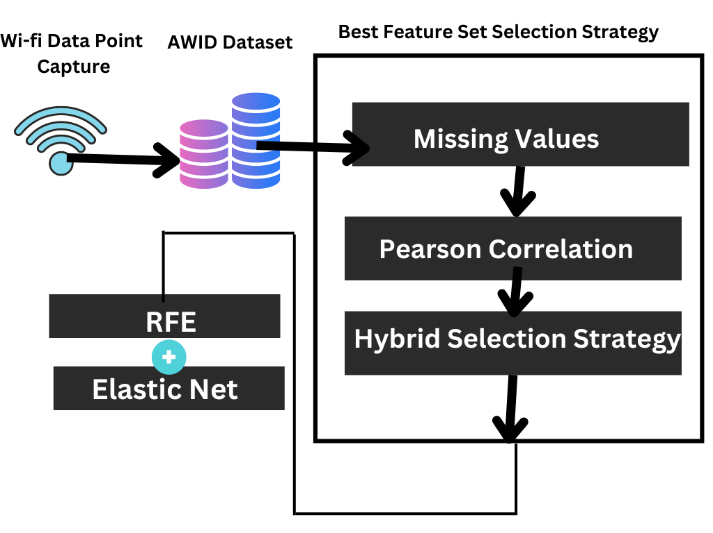
One of today's most promising developments is wireless networking, as it enables people across the globe to stay connected. As the wireless networks' transmission medium is open, there are potential issues in safeguarding the privacy of the information. Though several security protocols exist in the literature for the preservation of information, most cases fail with a simple spoof attack. So, intrusion detection systems are vital in wireless networks as they help in the identification of harmful traffic. One of the challenges that exist in wireless intrusion detection systems (WIDS) is finding a balance between accuracy and false alarm rate. The purpose of this study is to provide a practical classification scheme for newer forms of attack. The AWID dataset is used in the experiment, which proposes a feature selection strategy using a combination of Elastic Net and recursive feature elimination. The best feature subset is obtained with 22 features, and a deep deterministic policy gradient learning algorithm is then used to classify attacks based on those features. Samples are generated using the Euclidean Jacobian-based Saliency Map Attack (EJSMA) to evaluate classification outcomes using adversarial samples. The meta-analysis reveals improved results in terms of feature production (22 features), classification accuracy (98.75% for testing samples and 85.24% for adversarial samples), and false alarm rates (0.35%).
Article Details
References
Mohamed, A.B., Idris, N.B., Shanmugum, B.: A brief introduction to intrusion detection systems. In: International Conference on Intelligent Robotics, Automation, andManufacturing, pp. 263–271. Springer, Berlin (2012). https://doi.org/10.1007/978-3-642-35197-6_29.
Ranjit Panigrahi, Samarjeet Borah, Moumita Pramanik, Akash Kumar Bhoi, Paolo Barsocchi, Soumya Ranjan Nayak, Waleed Alnumay. Intrusion detection in cyber–physical environment using hybrid Naïve Bayes—Decision table and multi-objective evolutionary feature selection, Computer Communications,Volume 188,2022, Pages 133-144, ISSN 0140-3664, https://doi.org/10.1016/j.comcom.2022.03.009.
Buczak, A.L., Guven, E.: A survey of data mining and machine learning methods for cyber security intrusion detection. IEEE Commun. Surv. Tutor. 18(2), 1153–1176 (2016). https://doi.org/10.1109/COMST.2015.2494502
Singh, K.P., Kesswani, N. An Anomaly-Based Intrusion Detection System for IoT Networks Using Trust Factor. SN COMPUT. SCI. 3, 168 (2022). https://doi.org/10.1007/s42979-022-01053-9
Kuang, F.,Xu,W., Zhang, S.:Anovel hybrid KPCA and SVM with GAmodel for intrusion detection. Appl. Soft Comput. 18, 178–184 (2014)
Reddy, R.R., Ramadevi, Y., Sunitha, K.V.N.: Effective discriminant function for intrusion detection using SVM. In: Proceedings of International Conference on Advance in Computing, Communication and Information (ICACCI), pp. 1148–1153 (2016)
Li, W., Yi, P., Wu, Y., Pan, L., Li, J.: A new intrusion detection system based on KNN classification algorithm in wireless sensor network. J. Electron. Comput. Eng. 2014, 240217 (2014)
Bivens, A., Palagiri, C., Smith, R., Szymanski, B., Embrechts, M.: Network-based intrusion detection using neural networks. Intell. Eng. Syst. Artif. Neural Netw. 12(1), 579–584 (2002)
Quinlan, R.: Induction of decision trees.Mach. Learn. 1(1), 81–106(1986)
Ross Quinlan, J.: C4.5: Programs for Machine Learning. Morgan Kaufmann, Burlington (1993)
Vijayakumar, D.S., Ganapathy, S. Multistage Ensembled Classifier for Wireless Intrusion Detection System. Wireless Pers Commun 122, 645–668 (2022). https://doi.org/10.1007/s11277-021-08917-y
Javaid,A., Niyaz, Q., Sun,W.,Alam, M.:Adeep learning approach for network intrusion detection system. In: Proceedings of the 9th EAI International Conference on Bio-inspired Information and Communications Technologies (BICT), pp. 21–26 (2015)
Yin, C., Zhu, Y., Fei, J., He, X.: A deep learning approach for intrusion detection using recurrent neural networks. IEEE Access 5, 21954–21961 (2017). https://doi.org/10.1109/ACCESS.2017.2762418
Mnih, V., et al.: Human-level control through deep reinforcement learning. Nature 518, 529–533 (2015). https://doi.org/10.1038/nature14236
Mahmud, M., Kaiser, M.S., Hussain, A., Vassanelli, S.: Applications of deep learning and reinforcement learning to biological data. IEEE Trans. Neural Netw. Learn. Syst. 29(6), 2063–2079 (2018). https://doi.org/10.1109/TNNLS.2018.2790388
Kober, J., Bagnell, J.A., Peters, J.: Reinforcement learning in robotics: a survey. Int. J. Robot. Res. 32(11), 1238–1274 (2013).https://doi.org/10.1177/0278364913495721
C. Kolias, G. Kambourakis, A. Stavrou, and S. Gritzalis, "Intrusion detection in 802.11 networks: empirical evaluation of threats and a public dataset," IEEE Communications Surveys & Tutorials, vol. 18, no. 1, pp. 184-208, 2016.
Kamble, V. S. ., Khampariya, P. ., & Kalage, A. A. . (2023). A Survey on the Development of Real-Time Overcurrent Relay Coordination Using an Optimization Algorithm. International Journal of Intelligent Systems and Applications in Engineering, 11(3s), 104–114. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2537
Yin, C.; Zhu, Y.; Fei, J.; He, X. A Deep Learning Approach for Intrusion Detection Using Recurrent Neural Networks. IEEE Access 2017, 5, 21954–21961. doi: 10.1109/ACCESS.2017.2762418
Kim, G.; Lee, S.; Kim, S. A novel hybrid intrusion detection method integrating anomaly detection with misuse detection. Expert Syst. Appl. 2014, 41, 1690–1700. doi: 10.1016/j.eswa.2013.08.066
Tahir, H.M.; Said, A.M.; Osman, N.H.; Zakaria, N.H.; Sabri, P.N.A.M.; Katuk, N. Oving K-means clustering using discretization technique in network intrusion detection system. In Proceedings of the 3rd International Conference on Computer and Information Sciences (ICCOINS), Kuala Lumpur, Malaysia, 15–17 August 2016; pp. 248–2 doi: 10.1109/ICCOINS.2016.7783222
Alavizadeh, H.; Alavizadeh, H.; Jang-Jaccard, J. Deep Q-Learning Based Reinforcement Learning Approach for Network Intrusion Detection. Computers 2022, 11, 41. https://doi.org/10.3390/computers11030041
Javaid,A., Niyaz, Q., Sun,W.,Alam, M.:Adeep learning approach for network intrusion detection system. In: Proceedings of the 9th EAI International Conference on Bio-inspired Information and Communications Technologies (BICT), pp. 21–26 (2015)
Guillermo Caminero, Manuel Lopez-Martin, Belen Carro, Adversarial environment reinforcement learning algorithm for intrusion detection, Computer Networks, Volume 159, 2019,Pages 96-109, ISSN 1389-1286, https://doi.org/10.1016/j.comnet.2019.05.013.
Roderick,M., MacGlashan, J.: Implementing the deep Q-network. Stefanie Tellex, Humans To Robots Laboratory, Brown University, Providence, RI 02912, CoRR (2017)
Mark White, Kevin Hall, Ana Silva, Ana Rodriguez, Laura López. Predicting Educational Outcomes using Social Network Analysis and Machine Learning . Kuwait Journal of Machine Learning, 2(2). Retrieved from http://kuwaitjournals.com/index.php/kjml/article/view/182
RotaBulò, S., Biggio, B., Pillai, I., Pelillo,M., Roli, F.: Randomized prediction games for adversarial machine learning. IEEE Trans. Neural Netw. Learn. Syst. 28(11), 2466–2478 (2017). https://doi. org/10.1109/TNNLS.2016.2593488
Biggio, B., Fumera, G., Roli, F.: Security evaluation of pattern classifiers under attack. IEEE Trans. Knowl. Data Eng. 26(4), 984–996 (2014). https://doi.org/10.1109/TKDE.2013.57
Biggio, B., et al.: Security evaluation of support vector machines in adversarial environments. In: Ma,Y., Guo, G. (eds.) SupportVector Machines Applications, pp. 105–153. Springer, Cham (2014)
Papernot, N., McDaniel, P.,Wux, X., Jhax, S., Swamiz, A.: Distillation as a defense to adversarial perturbations against deep neural networks. CoRR (2016). https://doi.org/10.1109/SP.2016.41.
Pattanaik, A., Tang, Z., Liu, S., Bommannan, G., Chowdhary, G.: Robust Deep Reinforcement Learning with Adversarial Attacks. University of Illinois at Urbana-Champaign, CoRR (2017)
Wang, Z.: Deep learning-based intrusion detection with adversaries. IEEE Access 6, 38367–38384 (2018)
Blowers, M., Williams, J.: Machine learning applied to cyber operations. In: Network Science and Cybersecurity, pp. 55–175. Springer, New York (2014)
Farnaaz, N., Jabbar, M.A.: Random forest modelling for network intrusion detection system. Procedia Comput. Sci. 89, 213–217 (2016)
Pallathadka, D. H. . (2021). Mining Restaurant Data to Assess Contributions and Margins Data . International Journal of New Practices in Management and Engineering, 10(03), 06–11. https://doi.org/10.17762/ijnpme.v10i03.128
Tajbakhsh, A., Rahmati,M., Mirzaei, A.: Intrusion detection using fuzzy association rules. Appl. Soft Comput. 9, 462–469 (2009)
Polikar, R.: Ensemble based systems in decision making. IEEE Circuits Syst. Mag. 6(3), 21–45 (2006). https://doi.org/10.1109/MCAS.2006.1688199
Gharibian, F., Ghorbani, A.: Comparative study of supervised machine learning techniques for intrusion detection. In: Fifth Annual Conference on Communication Networks and Services Research (CNSR’07), pp. 350–358 (2007)
Zhang, J., Zulkernine, M., Haque, A.: Random-forests-based network intrusion detection systems. IEEE Trans. Syst. Man Cybern.C Appl. Rev. 38(5), 649–659 (2008). https://doi.org/10.1109/ TSMCC.2008.923876
Mukkamalla, S., Sung, A.H., Abhraham, A.: Intrusion detection using an ensemble of intelligent paradigms. J. Netw.Comput.Appl. 28, 167–182 (2005)
Shone, N., Ngoc, T.N., Phai, V.D., Shi, Q.: A deep learning approach to network intrusion detection. IEEE Trans. Emerg. Topics Comput. Intell. 2(1), 41–50 (2018). https://doi.org/10.1109/ TETCI.2017.277279210.1109/TETCI.2017.2772792
A. Servin, Multi-Agent Reinforcement Learning for Intrusion Detection. Ph.D. thesis, University of York, 2009.
K. Malialis, Distributed Reinforcement Learning for Network Intrusion Response. Ph.D. thesis, University of York, 2014
Kumar, N., Swain, S.N., Siva Ram Murthy, C.: A novel distributed Q-learning based resource reservation framework for facilitating D2D content access requests in LTE-A networks. IEEE Trans. Netw. Serv. Manag. 15(2), 718–731 (2018). https://doi.org/10.1109/TNSM.2018.2807594
Google Inc.: OpenAI and Pennsylvania State University, a repository for cleverhans library [Github Repository]. https://github.com/tensorflow/cleverhans (2016). Accessed 4 May 2022
Parker, L.R., Yoo, P.D., Asyhari, T.A., Chermak, L., Jhi, Y., Taha, K., 2019. Demise: interpretable deep extraction and mutual information selection techniques for iot intrusion detection, in: Proceedings of the 14th International Conference on Availability, Reliability and Security, pp. 1–10. doi:10.1145/3339252.3340497.
Ran, J., Ji, Y., Tang, B., 2019. A semi-supervised learning approach to ieee 802.11 network anomaly detection, in: 2019 IEEE 89th Vehicular Technology Conference (VTC2019-Spring), IEEE. pp. 1–5. doi:10. 1109/VTCSpring.2019.8746576
Alotaibi, B., Elleithy, K., 2016. A majority voting technique for wireless intrusion detection systems, in: 2016 IEEE Long Island Systems, Applications and Technology Conference (LISAT), IEEE. pp. 1–6. doi:10.1109/LISAT.2016.7494133
Thanthrige, U.S.K.P.M., Samarabandu, J., Wang, X., 2016. Machine learning techniques for intrusion detection on public dataset, in: 2016 IEEE Canadian Conference on Electrical and Computer Engineering (CCECE), IEEE. pp. 1–4. doi:10.1109/CCECE.2016.7726677.
Vaca, F.D., Niyaz, Q., 2018. An ensemble learning based wi-fi network intrusion detection system (wnids), in: 2018 IEEE 17th International Symposium on Network Computing and Applications (NCA), IEEE. pp. 1–5. doi:10.1109/NCA.2018.8548315
Mikhail, J.W., Fossaceca, J.M., Iammartino, R.: A semi-boosted nested model with sensitivity-based weighted binarization for multi-domain network intrusion detection.ACMTrans. Intell. Syst. Technol. 10, 1–27 (2017). https://doi.org/10.1145/3313778
Blanco, R., Cilla, J.J., Briongos, S., Malagon, P., Moya, J.M.: Applying cost-sensitive classifiers with reinforcement learning to IDS. In: International Conference on Intelligent Data Engineering and Automated Learning, pp. 531–538. Springer, Berlin (2018). https://doi.org/10.1016/j.neucom.2019.02.056
L. Nie et al., "Intrusion Detection in Green Internet of Things: A Deep Deterministic Policy Gradient-Based Algorithm," in IEEE Transactions on Green Communications and Networking, vol. 5, no. 2, pp. 778-788, June 2021, doi: 10.1109/TGCN.2021.3073714.
Singh, P., Ranga, V. Attack and intrusion detection in cloud computing using an ensemble learning approach. Int. j. inf. tecnol. 13, 565–571 (2021). https://doi.org/10.1007/s41870-020-00583-w