Deep Neural Network Solution for Detecting Intrusion in Network
Main Article Content
Abstract
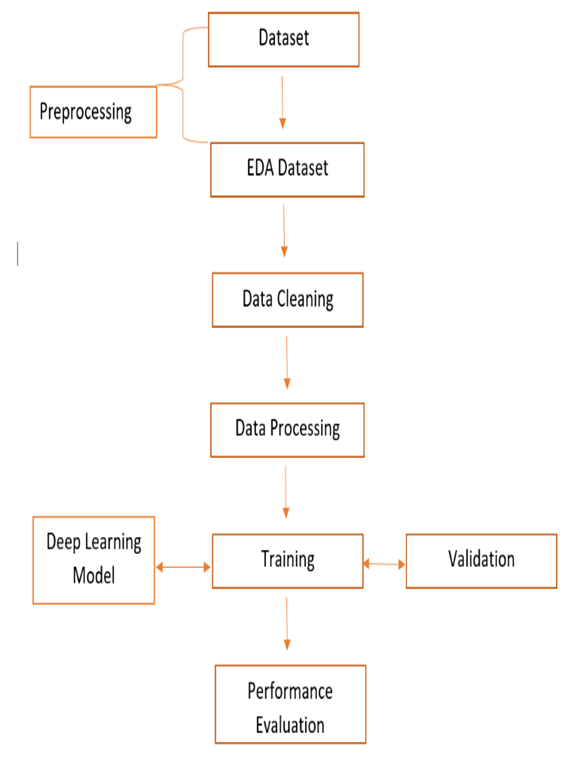
In our experiment, we found that deep learning surpassed machine learning when utilizing the DSSTE algorithm to sample imbalanced training set samples. These methods excel in terms of throughput due to their complex structure and ability to autonomously acquire relevant features from a dataset. The current study focuses on employing deep learning techniques such as RNN and Deep-NN, as well as algorithm design, to aid network IDS designers. Since public datasets already preprocess the data features, deep learning is unable to leverage its automatic feature extraction capability, limiting its ability to learn from preprocessed features. To harness the advantages of deep learning in feature extraction, mitigate the impact of imbalanced data, and enhance classification accuracy, our approach involves directly applying the deep learning model for feature extraction and model training on the existing network traffic data. By doing so, we aim to capitalize on deep learning's benefits, improving feature extraction, reducing the influence of imbalanced data, and enhancing classification accuracy.
Article Details
References
S,Rajendra, Bandre and J. N. Nandimath. "Design consideration of Network Intrusion detection system using Hadoop and GPGPU." Pervasive Computing (ICPC), 2015 International Conference on. IEEE, 2015.
CAI, Zeng-yu. "Development of intelligent intrusion detection based on biosimulation [J]." Journal of Zhengzhou University of Light Industry (Natural Science) 2 (2010): 018.
Kaushik,(2023).Deep Learning Unveils Hidden Insights: Advancing Brain Tumor Diagnosis. International Journal for Global Academic & Scientific Research, 2(2), 01–22. https://doi.org/10.55938/ijgasr.v2i2.45
Juszczyszyn, Krzysztof, et al. "Agent-based approach for distributed intrusion detection system design." International Conference on Computational Science. Springer, Berlin, Heidelberg, 2006.
Kulariya, Manish, et al. "Performance analysis of network intrusion detection schemes using Apache Spark." Communication and Signal Processing (ICCSP), 2016 International Conference on. IEEE, 2016.
Patcha, Animesh, and Jung-Min Park. "An overview of anomaly detection techniques: Existing solutions and latest technological trends." Computer networks 51.12 (2007): 3448-3470
Kaushik, P. (2023). Congestion Articulation Control Using Machine Learning Technique. Amity Journal of Professional Practices, 3(01). https://doi.org/10.55054/ajpp.v3i01.631
Devarakonda, Nagaraju, et al. "Intrusion detection system using bayesian network and hidden markov model." Procedia Technology 4 (2012): 506-514.
Rathore, R. (2022). A Study on Application of Stochastic Queuing Models for Control of Congestion and Crowding. International Journal for Global Academic & Scientific Research, 1(1), 1–6. https://doi.org/10.55938/ijgasr.v1i1.6
Benaicha, S. Eddine, et al. "Intrusion detection system using genetic algorithm." Science and Information Conference (SAI), 2014. IEEE, 2014.
Singh Choudhary, S. ., Ghosh, S. K. ., Rajesh, A. ., Alfurhood, B. S. ., Limkar, S. ., & Gill, J. . (2023). BotNet Prediction in Social Media based on Feature Extraction with Classification using Machine Learning Algorithms. International Journal of Intelligent Systems and Applications in Engineering, 11(3s), 150 –. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2553
P.S.Rathore, S. (2023). Analysing the efficacy of training strategies in enhancing productivity and advancement in profession: theoretical analysis in Indian context. International Journal for Global Academic & Scientific Research, 2(2), 56–77. https://doi.org/10.55938/ijgasr.v2i2.49
Dong, Shi, D.D. Zhou, and W. Ding. "The study of network traffic identification based on machine learning algorithm." Computational Intelligence and Communication Networks (CICN), 2012 Fourth International Conference on. IEEE, 2012.
Rathore, R. (2022). A Review on Study of application of queueing models in Hospital sector. International Journal for Global Academic & Scientific Research, 1(2), 1–6. https://doi.org/10.55938/ijgasr.v1i2.11
Shanmugavadivu, R., and N. Nagarajan. "Network intrusion detection system using fuzzy logic." Indian Journal of Computer Science and Engineering (IJCSE) 2.1 (2011): 101-111.
Sharafaldin, Iman, A.H.Lashkari, and Ali A. Ghorbani. "Toward Generating a New Intrusion Detection Dataset and Intrusion Traffic Characterization." ICISSP. 2018.
P.S.Rathore, S. (2023). The Impact of AI on Recruitment and Selection Processes: Analysing the role of AI in automating and enhancing recruitment and selection procedures. International Journal for Global Academic & Scientific Research, 2(2), 78–93. https://doi.org/10.55938/ijgasr.v2i2.50
Analysing the efficacy of training strategies in enhancing productivity and advancement in profession: theoretical analysis in Indian context. International Journal for Global Academic & Scientific Research, 2(2), 56–77. https://doi.org/10.55938/ijgasr.v2i2.49
Singh, A.Pal, and M. D.Singh. "Analysis of host-based and network-based intrusion detection system." International Journal of Computer Network and Information Security 6.8 (2014): 41-47.
Kaushik, P (2022). Role and Application of Artificial Intelligence in Business Analytics: A Critical Evaluation. International Journal for Global Academic & Scientific Research, 1(3), 01–11. https://doi.org/10.55938/ijgasr.v1i3.15
Sung, H.Andrew, and S.Mukkamala. "Identifying important features for intrusion detection using support vector machines and neural networks." Applications and the Internet, 2003. Proceedings. 2003 Symposium on. IEEE, 2003.
Takkellapati, V.Suneetha, and G. V. S. N. R. V. Prasad. "Network intrusion detection system based on feature selection and triangle area support vector machine." International Journal of Engineering Trends and Technology3.4 (2012).
Rathore, R. (2023). A Study Of Bed Occupancy Management In The Healthcare System Using The M/M/C Queue And Probability. International Journal for Global Academic & Scientific Research, 2(1), 01–09. https://doi.org/10.55938/ijgasr.v2i1.36
Ragsdale, J. Daniel , et al. "Adaptation techniques for intrusion detection and intrusion response systems." Systems, Man, and Cybernetics, 2000 IEEE International Conference on. Vol. 4. IEEE, 2000.
Harsh, S. ., Singh , D., & Pathak , S. (2021). Efficient and Cost-effective Drone – NDVI system for Precision Farming. International Journal of New Practices in Management and Engineering, 10(04), 14–19. https://doi.org/10.17762/ijnpme.v10i04.126
Shanmugam, Bharanidharan, and N.BashahIdris. "Improved intrusion detection system using fuzzy logic for detecting anomaly and misuse type of attacks." Soft Computing and Pattern Recognition, 2009. SOCPAR'09. International Conference of. IEEE, 2009.
Singh, Shubhangi, and R.S.Kushwah. "A Study on Intrusion Detection in Wireless Networks by Using Genetic Algorithm Applications." Computational Intelligence and Communication Networks (CICN), 2014 International Conference on. IEEE, 2014.
Kaushik, P. (2023). Artificial Intelligence Accelerated Transformation in The Healthcare Industry. Amity Journal of Professional Practices, 3(01). https://doi.org/10.55054/ajpp.v3i01.630
" Upasani, Nilam, and HariOm. "Evolving fuzzy min-max neural network for outlier detection." Procedia computer science 45 (2015): 753-761.
Wu, Zheng, et al. "Automated intrusion response decision based on the analytic hierarchy process." Knowledge Acquisition and Modeling Workshop, 2008. KAM Workshop 2008. IEEE International Symposium on. IEEE, 2008.
Kaushik, P. (2023). Unleashing the Power of Multi-Agent Deep Learning: Cyber-Attack Detection in IoT. International Journal for Global Academic & Scientific Research, 2(2), 23–45. https://doi.org/10.55938/ijgasr.v2i2.46
Xiang, Junlong, et al. "Using extreme learning machine for intrusion detection in a big data environment." Proceedings of the 2014 Workshop on Artificial Intelligent and Security Workshop. ACM, 2014.
Xiaodong, W., et al. "Development of a snort-based security network management and real-time intrusion detection system." Journal-Beijing Normal University Natural Science Edition 40.1 (2004): 40-43.
Zhang, Yongguang, Wenke Lee, and Yi-An Huang. "Intrusion detection techniques for mobile wireless networks." Wireless Networks 9.5 (2003): 545-556.
Zikopoulos, Paul, and Chris Eaton. Understanding big data: Analytics for enterprise class hadoop and streaming data. McGraw-Hill Osborne M.