Novel Proposed Work for Empirical Word Searching in Cloud Environment
Main Article Content
Abstract
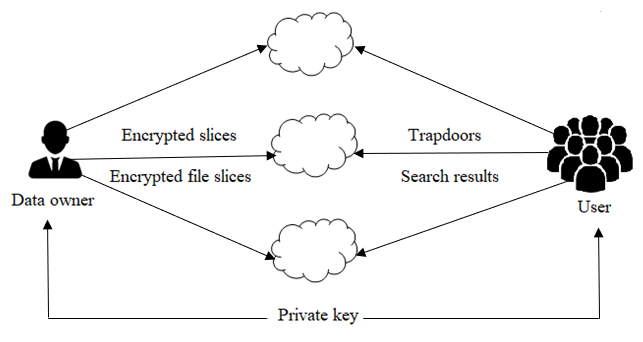
People's lives have become much more convenient as a result of the development of cloud storage. The third-party server has received a lot of data from many people and businesses for storage. Therefore, it is necessary to ensure that the user's data is protected from prying eyes. In the cloud environment, searchable encryption technology is used to protect user information when retrieving data. The versatility of the scheme is, however, constrained by the fact that the majority of them only offer single-keyword searches and do not permit file changes.A novel empirical multi-keyword search in the cloud environment technique is offered as a solution to these issues. Additionally, it prevents the involvement of a third party in the transaction between data holder and user and guarantees integrity. Our system achieves authenticity at the data storage stage by numbering the files, verifying that the user receives a complete ciphertext. Our technique outperforms previous analogous schemes in terms of security and performance and is resistant to inside keyword guessing attacks.The server cannot detect if the same set of keywords is being looked for by several queries because our system generates randomized search queries. Both the number of keywords in a search query and the number of keywords in an encrypted document can be hidden. Our searchable encryption method is effective and protected from the adaptive chosen keywords threat at the same time.
Article Details
References
Yunhong Zhou, Shihui Zheng, and Licheng Wang, "Privacy-Preserving and Efficient Public Key Encryption with Keyword Search-Based CP-ABE in Cloud", MDPI cryptography,,VOl(4), Issue 28; doi:10.3390/cryptography404002813 October 2020.
Qingji Zheng Shouhuai Xu Giuseppe Ateniese, "VABKS: Verifiable Attribute-based Keyword Search over Outsourced Encrypted Data", IEEE INFOCOM 2014 - IEEE Conference on Computer Communications. 978-14799-3360-0/14/$31.00 ©2014 IEEE
Zabiha Khan,Kamala Kumari, B. K, Rumana Iffath, Saima Ahmed, Zaiba Tabassum, "Review of Attribute-based Keyword Search Authorization in Cloud", INTERNATIONAL JOURNAL OF ENGINEERING RESEARCH & TECHNOLOGYwww.ijert.orgNConPCS - 2017 Conference Proceedings Special Issue - 2017.
XINRUI GE, JIA YU, CHENGYU HU, HANLIN ZHANG, AND RONG HAO, "Enabling Efficient Verifiable Fuzzy Keyword Search Over Encrypted Data in Cloud Computing", IEEE Access volume 6 September 7, 2018. Digital Object Identifier 10.1109/ACCESS.2018.2866031
Lincei, Chungen Xu, Lei Xiaoling Yu, and Cong Zuo, "Verifiable Identity-Based Encryption with Keyword Search for IoT from Lattice", Computers, Materials & Continua Tech Science Press, CMC, 2021, vol.68, no.2 . DOI:10.32604/cmc.2021.017216
Shangping Wang, Jian Ye, Yaling Zhang, China, "A keyword searchable attribute-based encryption scheme with attribute update for cloud storage" PLOS ONE | https://doi.org/10.1371/journal.pone.0197318 May 24, 2018 May 24, 2018.
Rui Zhang, Rui Xue, Ting Yuyz, and Ling Linux, "PVSAE: A Public Verifiable Searchable Encryption Service Framework for Outsourced Encrypted Data", 2016 IEEE International Conference on Web Services (ICWS) DOI:10.1109/ICWS.2016.62
A Shiny, Jayanth Das, M Venkat Aravind, C A Anirudh Srivatsaa, M Rahul, "Cloud Server Misbehavior Detection Using Ranked Keyword Search Results Verification", International Journal of Engineering and AdvancedTechnology (IJEAT) ISSN: 2249 – 8958, Volume-8 Issue-4, April 2019.
R. SaiVenkata Siva Kumar, T.P.Anithaashri, "Enhancement Of Cloud Data Search Using Symmetric-Key Based Verification", Chennai, anithaashritp.sse@saveetha.com, European Journal of Molecular & Clinical Medicine ISSN 2515-8260 Volume 07, Issue 08, 2020.
Devi Thiyagarajan, R. Ganesan, "USER VERIFIABLE MULTIPLE KEYWORD SEARCH SCHEME USING THE MERKLE TREE FOR OUTSOURCED DATA IN THE CLOUD", International Journal of Technology (2017) 4: 591-600 ISSN 2086-9614.
Christopher Davies, Matthew Martine, Catalina Fernández, Ana Flores, Anders Pedersen. Improving Automated Essay Scoring with Machine Learning Techniques. Kuwait Journal of Machine Learning, 2(1). Retrieved from http://kuwaitjournals.com/index.php/kjml/article/view/173
Chongqing Hu, Wei Li, ,Xiuzhen Cheng, Jiguo Yu, Shengling Wang, and RongfangBie, "A Secure and Verifiable Access Control Scheme for Big Data Storage in Clouds", IEEE Transaction on BIG DATA VOL 4 no 3 sep 2018 .
Junxiong Wang Xin Wang Hui Li Xidian University, "A Secure and Veri?able Outsourced Access ControlScheme in Fog-Cloud Computing", Xidian University, Xi’an 710071, China; Security and Privacy Challenges in Emerging Fog Computing) July 2017. ; https://doi.org/10.3390/s17071695
Shubhashis Sengupta Accenture Technology Labs No.4/1, IBC Knowledge Park Bannerghatta Road, Bangalore "Cloud Computing Security – Trends and Research Directions", Conference Paper · July 2011.
Roshni Rajendran, Vani V Prakash, "An Efficient Ranked Multi-Keyword Search for Multiple Data Owners Over Encrypted Cloud Data: Survey", International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 Volume: 05 Issue: 09 | Sep 2018.
M. Thangamani, Dr. P. Thangaraj, Fuzzy Ontology for Document Clustering based on Genetic Algorithm, Applied Mathematics and Information Science, Vol. 4, Issue 7, pp.1563-1574, 2013, ISSN 2325-0399.
4. B. Prabhu Kavin, Sagar Karki S. Hemalatha, Deepmala Singh, R. Vijayalakshmi,M.Thangamani,SulaimaLebbe Abdul Haleem, Deepa Jose, Vineet Tirth,Pravin R. Kshirsagar , and Amsalu GosuAdigo “Machine Learning-Based Secure Data Acquisition for Fake Accounts Detection in Future Mobile Communication Networks “Wireless Communications and Mobile Computing Volume 2022, Article ID 6356152, 10 pages https://doi.org/10.1155/2022/6356152.
Rexhepi, B. R. ., Kumar, A. ., Gowtham, M. S. ., Rajalakshmi, R. ., Paikaray, D. ., & Adhikari, P. K. . (2023). An Secured Intrusion Detection System Integrated with the Conditional Random Field For the Manet Network. International Journal of Intelligent Systems and Applications in Engineering, 11(3s), 14–21. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2526
Aziz Makandar, Rashmi.Somshekhar, Sankhya Homey - A Key-Policy AAttribute-based temporary Keyword Search Scheme for Secure Cloud Storage", International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 Volume: 06 Issue: 06 | June 2019 www.irjet.net p-ISSN: 2395-0072 © 2019, IRJET
Xiangfu Song, Changyu Dong, Dandan Yuan, Qiuliang Xu and Minghao Zhao, "Forward Private Searchable SymmetricEncryption with Optimized I/O Efficiency", Published in: IEEE Transactions on Dependable and Secure Computing Issue: 5, Sept.-Oct. 1 2020.
Dr. Nitin Sherje. (2020). Biodegradable Material Alternatives for Industrial Products and Goods Packaging System. International Journal of New Practices in Management and Engineering, 9(03), 15 - 18. https://doi.org/10.17762/ijnpme.v9i03.91
S. Hemalatha, K.V.Kanimozhi,G. Nagappan, P. C. Senthil Mahesh, R. Priya, M. Vidhya “Atomizing E-Government Facilities Using Big Data Analytic “ ECS Transactions, 107 (1) 17323-17333 (2022) 10.1149/10701.17323ecst ©The Electrochemical Societ
SulaimaLebbe Abdul Haleem, Pravin R. Kshirsagar, Hariprasath Manoharan BoppuruRudra Prathap, Hemalatha S, Kukatlapalli Pradeep Kumar, Vineet Tirth, Saiful Islam,RaghuveerKatragadda,and Temesgen AbetoAmibo “ Wireless Sensor Data Acquisition and Control Monitoring Model for Internet of Things Applications “ Scienti?c Programming Volume 2022, Article ID 9099163, 9 pages s://doi.org/10.1155/2022/9099163.
Jianfeng Wang, Hua Ma, Qiang Tang, and Jin Li, "Efficient Verifiable Fuzzy Keyword Search over Encrypted Data in Cloud Computing", April 2013Computer Science and Information Systems 10(2):667-684 DOI:10.2298/CSIS121104028W.
Kai Nie, Yunling Wang, and Xiaoling Tao, "Efficient publicly verifiable conjunctive keyword search over encrypted data in cloud computing", December 4, 2019pp 707-718.
Xiuxiu Jiang, Jia Yu, Jingbo Yan, Rong Hao, "Enabling efficient and verifiable multi-keyword ranked search over encrypted cloud data", an International Journal, Volume 403, Issue C, September 2017pp 22–41.
Qing Wang, Xi Zhang, Jing Qin, Jixin Ma, Xinyi Huang, "A Verifiable Symmetric Searchable Encryption Scheme Based on the AVL Tree", The Computer Journal, bxab152, https://doi.org/10.1093/comjnl/bxab152 on 08 October 2021.
Shridevi Chandraprakash Karande, Saba Aslam, "A Survey on Privacy-Preserving Ranked Multi-Keyword Search for Multiple Data Owners Over Encrypted Cloud Data", Published in International Journal of InnovativeResearch in Science, Engineering and 2017
Shufen Niu, Wenke Liu, Song Han, Lizhi Fang, et al, "A data-sharing scheme that supports multi-keyword search for electronic medical records", PLoS One. 2021 Jan 7;16(1): e0244979.
A.Swaminathan, Vivekanandan, P ,Sivajothi.E, "Anomaly Detection Model Based on Multivariate Correlation Analysis Technique to Detect Covert Communication in Wireless Sensor Network", Journal of Computational and Theoretical Nanoscience, Volume 13, Issue 8, pp. 1-7.(2016)
Charu Gandhi,Sayed Sayeed Ahmad, Abolfazl Mehbodniya, Julian ,S. Hemalatha, Haitham Elwahsh, and Basant Tiwari “ “Biosensor Assisted Method for Abdominal Syndrome Classification using Machine Learning Algorithm” Computational Intelligence and Neuroscience Volume 2022, Article ID 4454226, 14 pages https://doi.org/10.1155/2022/4454226.
P. Adlene Ebenezer, Sweta Pasayat, Sunny Sunan, "Verifying Fuzzy Keyword Search Over Cipher Text in Cloud Computing", International Journal of Engineering and Advanced Technology (IJEAT) ISSN: 2249 – 8958, Volume-9 Issue-1, October 2019.
Dr.P.Perumal , Mr.J.K.Periasamy , Dr.S.Hemalatha , K.V. Kanimozhi , Dr.Suman Madan , Dr.V.Subedha “ Trendy Technique To Solve Complex And Report Generation In Secured Distributed Cloud Environment “ Design Engineering, Volume 2021,Issue :6,7227- 7236, ISSN: 0011- 9342 , http://thedesignengineering.com/index.php/DE/issue/view/28.