An Adaptive Blockchain based Three-Tier Architecture in Fog based IoT for Personal Healthcare Data Application
Main Article Content
Abstract
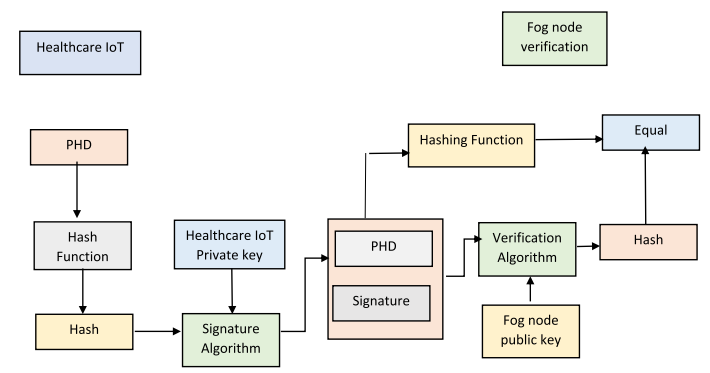
To protect patient health data (PHD) and ensure the security of healthcare IoT devices, this paper presents an Advanced Signature-Based Encryption algorithm (ASE), a blockchain analytical model, a mathematical framework, and an Adaptive Fog Computing based Three-tier Architecture (AFCTTA). The aim is to enable safe access to real-time services and IoT for end users. This AFCTTA was constructed on a blockchain platform, providing trustworthy data transmission between patients, clinicians, fog nodes, and IoT. Additionally, a decentralized fog computing-based blockchain analytical model along with a mathematical framework were produced to ensure secure transfer of data and transactions within healthcare IoT. To ensure secure communication between devices and fog nodes, a private block chain was implemented in order to validate certificates and keys. As an added security measure, an ASE method was devised. This algorithm utilizes War Optimization Strategy (WOA) to select optimal keys for securing data from heterogeneous and homogeneous IoT healthcare equipment. Through its encryption process utilizing various cryptographic techniques, all traffic is encrypted before being decrypted once it reaches its intended destination. To validate its proposed approach, UCI machine library is collecting health care data. To execute this method, Python is utilized and compared to traditional algorithms such as Rivest-Shamir-Adleman (RSA), Elliptical Curve Cryptography (ECC), and Tiny Lightweight Symmetric Encryption-Aquila Optimization Algorithm (TLSE-AOA).
Article Details
References
Y.I. Alzoubi, A. Al-Ahmad, A. Jaradat, “Fog computing security and privacy issues, open challenges, and blockchain solution: An overview”. International Journal of Electrical & Computer Engineering vol. 11, no. 6, pp. 2088-8708, 2021.
Y. Liu, J. Zhang, J. Zhan, “Privacy protection for fog computing and the internet of things data based on blockchain”. Cluster Computing, vol. 24, pp. 1331-45, 2021.
P. Kumar, R. Kumar, G.P. Gupta, R. Tripathi, “A Distributed framework for detecting DDoS attacks in smart contract?based Blockchain?IoT Systems by leveraging Fog computing”. Transactions on Emerging Telecommunications Technologies, vol. 32, no. 6, pp. e4112, 2021.
M.S. Eddine, M.A. Ferrag, O. Friha, L. Maglaras, “EASBF: An efficient authentication scheme over blockchain for fog computing-enabled internet of vehicles”. Journal of Information Security and Applications, vol. 59, pp. 102802, 2021.
A.W. Kiwelekar, P. Patil, L.D. Netak, S.U. Waikar, “Blockchain-based security services for fog computing”. Fog/Edge Computing for Security, Privacy, and Applications, pp. 271-90, 2021.
M. Kong, J. Zhao, X. Sun, Y. Nie, “Secure and efficient computing resource management in blockchain-based vehicular fog computing”. China Communications, vol. 18, no. 4, pp. 115-25, 2021.
J. Ofulue, M. Benyoucef, “Data monetization: insights from a technology-enabled literature review and research agenda”. Management Review Quarterly, pp. 1-45, 2022.
D. Garg, K.K. Bhatia, S. Gupta, “A Research Perspective on Security in Fog Computing Through Blockchain Technology. InArtificial Intelligence and Sustainable Computing for Smart City: First International Conference, AIS2C2 2021, Greater Noida, India, March 22–23, 2021, Revised Selected Papers” 1 2021, Springer International Publishing pp. 91-104, 2021.
R.T. Hasan, S.Y. Ameen, “Security Enhancement of IoT and Fog Computing Via Blockchain Applications.” Journal of Soft Computing and Data Mining, vol. 2, no. 2, pp. 26-38, 2021.
V.K. Quy, N.V. Hau, D.V. Anh, L.A. Ngoc, “Smart healthcare IoT applications based on fog computing: architecture, applications and challenges.” Complex & Intelligent Systems, vol. 8, no. 5, pp. 3805-15, 2022.
Y. Qu, L. Gao, T.H. Luan, Y. Xiang, S. Yu, B. Li, G. Zheng, “Decentralized privacy using blockchain-enabled federated learning in fog computing.” IEEE Internet of Things Journal, vol. 7, no. 6, pp. 5171-83, 2020.
A.A. Patwary, A. Fu, S.K. Battula, R.K. Naha, S. Garg, A. Mahanti, “FogAuthChain: A secure location-based authentication scheme in fog computing environments using Blockchain.” Computer Communications, vol. 162, pp. 212-24, 2020.
D. Ngabo, D. Wang, C. Iwendi, J.H. Anajemba, L.A. Ajao, C. Biamba, “Blockchain-based security mechanism for the medical data at fog computing architecture of internet of things.” Electronics, vol. 10, no. 17, pp. 2110, 2021.
T. Hewa, A. Braeken, M. Liyanage, M. Ylianttila, “Fog computing and blockchain-based security service architecture for 5G industrial IoT-enabled cloud manufacturing.” IEEE Transactions on Industrial Informatics, vol. 18, no. 10, pp. 7174-85, 2022.
O. Umoren, R. Singh, Z. Pervez, K. Dahal, “Securing Fog Computing with a Decentralised User Authentication Approach Based on Blockchain.” Sensors, vol. 22, no. 10, pp. 3956, 2022.
S. Shukla, S. Thakur, S. Hussain, J.G. Breslin, S.M. Jameel, “Identification and authentication in healthcare internet-of-things using integrated fog computing based blockchain model.” Internet of Things, vol. 15, pp. 100422, 2021.
D. Ngabo, Wang D, Iwendi C, Anajemba JH, Ajao LA, Biamba C, “Blockchain-based security mechanism for the medical data at fog computing architecture of internet of things.” Electronics, vol. 10, no. 17, pp. 2110, 2021.
A. Mehbodniya, J.L. Webber, R. Neware, F. Arslan, R.V. Pamba, M. Shabaz, “Modified Lamport Merkle Digital Signature blockchain framework for authentication of internet of things healthcare data.” Expert Systems, vol. 39, no. 10, pp. e12978, 2022.
T.S. Ayyarao, N.S. Ramakrishna, R.M. Elavarasan, N. Polumahanthi, M. Rambabu, G. Saini, B. Khan, B. Alatas, “War strategy optimization algorithm: a new effective metaheuristic algorithm for global optimization.” IEEE Access, vol. 10, pp. 25073-105, 2022.