Fuzzy TOPSIS-based Secure Neighbor Discovery Mechanism for Improving Reliable Data Dissemination in Wireless Sensor Networks
Main Article Content
Abstract
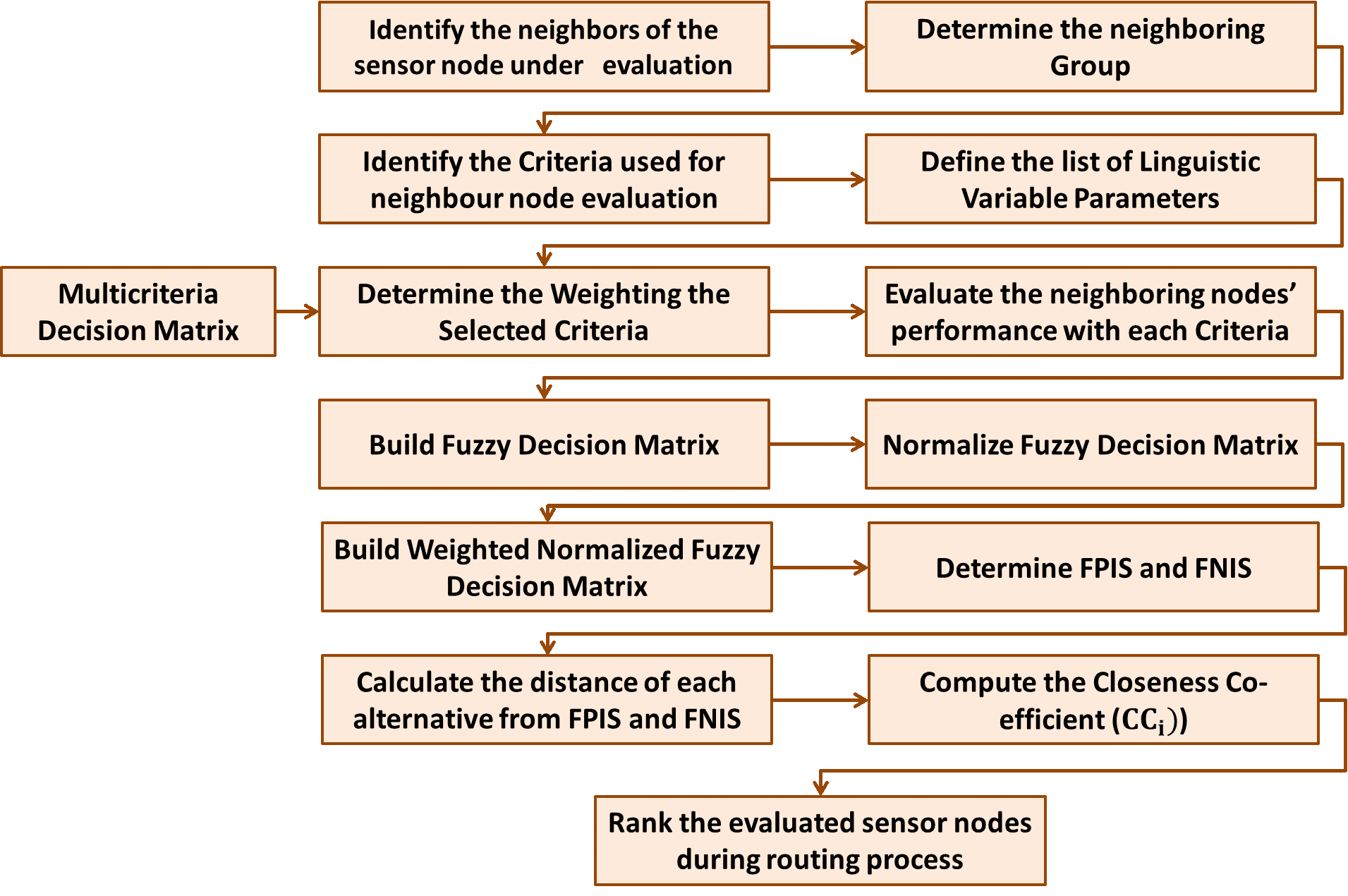
Wireless Sensor Networks (WSNs) being an indispensable entity of the Internet of Things (IoT) are found to be more and more widely utilized for the rapid advent of IoT environment. The reliability of data dissemination in the IoT environment completely depends on the secure neighbor discovery mechanism that are utilized for effective and efficient communication among the sensor nodes. Secure neighbor discovery mechanisms that significantly determine trustworthy sensor nodes are essential for maintaining potential connectivity and sustaining reliable data delivery in the energy-constrained self organizing WSN. In this paper, Fuzzy Technique of Order Preference Similarity to the Ideal Solution (TOPSIS)-based Secure Neighbor Discovery Mechanism (FTOPSIS-SNDM) is proposed for estimating the trust of each sensor node in the established routing path for the objective of enhancing reliable data delivery in WSNs. This proposed FTOPSIS-SNDM is proposed as an attempt to integrate the merits of Fuzzy Set Theory (FST) and TOPSIS-based Multi-criteria Decision Making (MCDM) approach, since the discovery of secure neighbors involves the exchange of imprecise data and uncertain behavior of sensor nodes. This secure neighbor is also influenced by the factors of packet forwarding potential, delay, distance from the Base Station (BS) and residual energy, which in turn depends on multiple constraints that could be possibly included into the process of secure neighbor discovery. The simulation investigations of the proposed FTOPSIS-SNDM confirmed its predominance over the benchmarked approaches in terms of throughput, energy consumption, network latency, communication overhead for varying number of genuine and malicious neighboring sensor nodes in network.
Article Details
References
Zhang, P., Wang, S., Guo, K., & Wang, J. (2018). A secure data collection scheme based on compressive sensing in wireless sensor networks. Ad Hoc Networks, 70, 73-84.
Merad Boudia, O. R., Senouci, S. M., &Feham, M. (2018). Secure and efficient verification for data aggregation in wireless sensor networks. International Journal of Network Management, 28(1), e2000.
Wang, J., & Chen, Y. (2018). Research and improvement of wireless sensor network secure data aggregation protocol based on SMART. International Journal of Wireless Information Networks, 25(3), 232-240.
Ambigavathi, M., & Sridharan, D. (2018). Energy-aware data aggregation techniques in wireless sensor network. Advances in power systems and energy management, 165-173.
Tolba, A. (2017) .Organizing multipath routing in cloud computing environments. Int J Adv Comput Sci Appl, 8(1), 455-462.?
A. Salem, D. ., & Hashim, E. M. . (2023). Impact of Data Pre-Processing on Covid-19 Diagnosis Using Machine Learning Algorithms. International Journal of Intelligent Systems and Applications in Engineering, 11(1s), 164–171. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2489
Stoleru, R., Wu, H., Chenji H. (2012. Secure neighbor discovery and wormhole localization in mobile ad hoc networks. Ad Hoc Netw, 10(7), 1179-1190.?
Kumar, G., Rai, M.K., & Saha, R. (2017). Securing range free localization against wormhole attack using distance estimation and maximum likelihood estimation in wireless sensor networks. J Netw Comput Appl, 99, 10-16.
Malik, S.K., Dave M., Dhurandher S.K., Woungang I. &Barolli, L. (2017). An ant-based QoS-aware routing protocol for heterogeneous wireless sensor networks. Soft Comput, 21(21), 6225-6236.?
Mr. Vaishali Sarangpure. (2014). CUP and DISC OPTIC Segmentation Using Optimized Superpixel Classification for Glaucoma Screening. International Journal of New Practices in Management and Engineering, 3(03), 07 - 11. Retrieved from http://ijnpme.org/index.php/IJNPME/article/view/30
Ahmed, A., Bakar, K.A., Channa, M.I., & Khan, A.W. (2016a). A secure routing protocol with trust and energy awareness for wireless sensor network. Mob Netw Appl, 21(2), 272-285.
Usman, A. B., & Gutierrez, J. (2018). Trust- based analytical models for secure wireless sensor networks. In Security and Privacy Management, Techniques, and Protocols, IGI Global, pp. 47-65.?
Zhang, B., Huang, Z., & Xiang, Y. (2014). A novel multiple-level trust management framework for wireless sensor networks. Comput Netw, 72, 45-61.
Xia, F., Liaqat, H.B., Ahmed, A.M., Liu, L., Ma, J., Huang, R., Tolba, A. (2016a). User popularity-based packet scheduling for congestion control in ad-hoc social networks. J Comput Syst Sci, 82(1), 93-112.
Esposito, M., Kowalska, A., Hansen, A., Rodríguez, M., & Santos, M. Optimizing Resource Allocation in Engineering Management with Machine Learning. Kuwait Journal of Machine Learning, 1(2). Retrieved from http://kuwaitjournals.com/index.php/kjml/article/view/115
Xia, H., Yu, J., Pan, Z.K., Cheng, X.G., & Sha E.H.M. (2016b). Applying trust enhancements to reactive routing protocols in mobile ad hoc networks. Wirel Netw, 22(7), 2239-2257.
Xia, H., Yu, J., Pan, Z.K., Cheng, X.G., & Sha E.H.M. (2016b). Applying trust enhancements to reactive routing protocols in mobile ad hoc networks. Wirel Netw, 22(7), 2239-2257.
AlFarraj, O., AlZubi, A., & Tolba, A. (2018). Trust-based neighbor selection using activation function for secure routing in wireless sensor networks. Journal of Ambient Intelligence and Humanized Computing, 1-11.
Khalid, N. A., Bai, Q., & Al-Anbuky, A. (2019). Adaptive trust-based routing protocol for large scale WSNs. IEEE Access, 7, 143539-143549.
Yang, J., He, S., Xu, Y., Chen, L., & Ren, J. (2019). A trusted routing scheme using blockchain and reinforcement learning for wireless sensor networks. Sensors, 19(4), 970.
Renjith, P. N. (2020). Towards secure data forwarding with anfis and trust evaluation in wireless sensor networks. Wireless Personal Communications, 114(1), 765-781.
Abd El-Moghith, I. A., & Darwish, S. M. (2021). Towards designing a trusted routing scheme in wireless sensor networks: A new deep blockchain approach. IEEE Access, 9, 103822-103834.
Hajiee, M., Fartash, M., & Eraghi, N. O. (2021). Trust-based Routing Optimization using Learning Automata in Wireless Sensor Network. Majlesi Journal of Electrical Engineering, 15(4), 87-98.
John, R., & Deepa, J. (2022, April). Trust Model for Secure Routing in Wireless Sensor Network using AI Technique. In 2022 8th International Conference on Smart Structures and Systems (ICSSS) (pp. 1-5). IEEE.
Goar, D. V. . (2021). Biometric Image Analysis in Enhancing Security Based on Cloud IOT Module in Classification Using Deep Learning- Techniques. Research Journal of Computer Systems and Engineering, 2(1), 01:05. Retrieved from https://technicaljournals.org/RJCSE/index.php/journal/article/view/9
Sajan, R. I., Christopher, V. B., Kavitha, M. J., & Akhila, T. S. (2022). An energy aware secure three-level weighted trust evaluation and grey wolf optimization based routing in wireless ad hoc sensor network. Wireless Networks, 28(4), 1439-1455.
Rahamat Basha, S., Sharma, C., Sayeed, F., Arularasan, A. N., Pramila, P. V., Shinde, S. K., Pant, B., Rajaram, A., &Yeshitla, A. (2022). Implementation of reliability antecedent forwarding technique using straddling path recovery in Manet. Wireless Communications and Mobile Computing, 2022(4), 1-9.
Hwang, C., & Yoon, K. (1981). Methods for multiple attribute decision making. Multiple Attribute Decision Making, 3(4), 58-191.
Shamsuzzoha, A., Piya, S., &Shamsuzzaman, M. (2021). Application of fuzzy TOPSIS framework for selecting complex project in a case company. Journal of Global Operations and Strategic Sourcing, 14(3), 528-566.
Gui, X., Wang, J., Wang, G., Park, J., & Sandhu, R. (2019). Dynamic trust evaluation model based on bidding and multi-attributes for social networks. International Journal of High Performance Computing and Networking, 13(4), 436.
Chen, Q., Liu, L., Yang, Z., & Guo, K. (2016). Prediction approach of critical node based on multiple attribute decision making for opportunistic sensor networks. Journal of Sensors, 2016(4), 1-8.
Jagatheswari, S., Ramalingam, P., & Chandra Priya, J. (2022). Improved grey relational analysis-based TOPSIS method for cooperation enforcing scheme to guarantee quality of service in MANETs. International Journal of Information Technology, 14(2), 887-897.
Katsikas, S., &Gkioulos, V. (2020). Security, privacy, and trustworthiness of sensor networks and Internet of things. Sensors, 20(14), 3846.
Wang, Z., Xu, G., Zhang, N., Qi, Z., Wei, F., & He, L. (2021). Ferry node identification model for the security of mobile ad hoc network. Security and Communication Networks, 2021(4), 1-13.