A Multilayer Approach for Intrusion Detection with Lightweight Multilayer Perceptron and LSTM Deep Learning Models
Main Article Content
Abstract
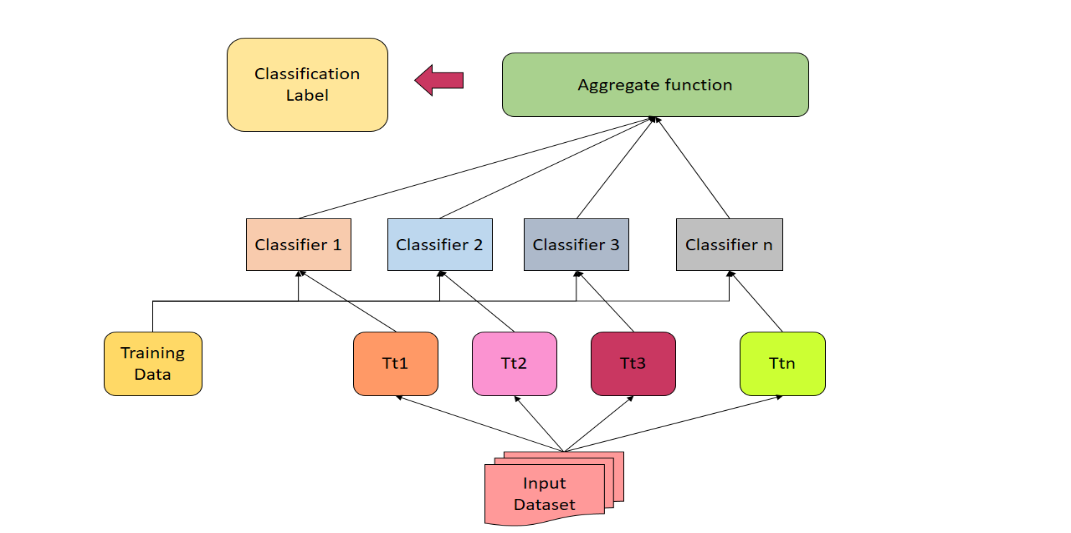
Intrusion detection is essential in the field of cybersecurity for protecting networks and computer systems from nefarious activity. We suggest a novel multilayer strategy that combines the strength of the Lightweight Multilayer Perceptron (MLP) and Long Short-Term Memory (LSTM) deep learning models in order to improve the precision and effectiveness of intrusion detection.The initial layer for extraction of features and representation is the Lightweight MLP. Its streamlined architecture allows for quick network data processing while still maintaining competitive performance. The LSTM deep learning model, which is excellent at identifying temporal correlations and patterns in sequential data, receives the extracted features after that.Our multilayer technique successfully manages the highly dimensional and dynamic nature of data from networks by merging these two models. We undertake extensive tests on benchmark datasets, and the outcomes show that our strategy performs better than conventional single-model intrusion detection techniques.The suggested multilayer method also demonstrates outstanding efficiency, which makes it particularly ideal for real-time intrusion detection in expansive network environments. Our multilayer approach offers a strong and dependable solution for identifying and reducing intrusions, strengthening the security position of computer systems and networks as cyber threats continue to advance.
Article Details
References
P. Ambika, “Machine learning and deep learning algorithms on the Industrial Internet of Things (IIoT),” Advances in Computers, vol. 117, no. 1, pp. 321–338, 2020.
R. Ashima, A. Haleem, S. Bahl, M. Javaid, S. K. Mahla, and S. Singh, “Automation and manufacturing of smart materials in Additive Manufacturing technologies using the Internet of Things towards the adoption of Industry 4.0,” Materials Today: Proceedings, vol. 45, pp. 5081–5088, 2021.
L. M. Gladence, V. M. Anu, R. Rathna, and E. Brumancia, “Recommender system for home automation using IoT and artificial intelligence,” Journal of Ambient Intelligence and Humanized Computing, pp. 1–9, 2020.
T. Sherasiya, H. Upadhyay, and H. B. Patel, “A survey: intrusion detection system for internet of things,” International Journal of Computer Science and Engineering (IJCSE), vol. 5, no. 2, pp. 91–98, 2016.
J. B. Awotunde, R. G. Jimoh, S. O. Folorunso, E. A. Adeniyi, K. M. Abiodun, and O. O. Banjo, “Privacy and security concerns in IoT-based healthcare systems,” Internet of Things, pp. 105–134, 2021.
E. A. Adeniyi, R. O. Ogundokun, and J. B. Awotunde, “IoMT-based wearable body sensors network healthcare monitoring system,” in IoT in Healthcare and Ambient Assisted Living, pp. 103–121, Springer, Singapore, 2021.
K. Amit and C. Chinmay, “Artificial intelligence and Internet of Things based healthcare 4.0 monitoring system,” Wireless Personal Communications, pp. 1–14, 2021.
F. E. Ayo, S. O. Folorunso, A. A. Abayomi-Alli, A. O. Adekunle, and J. B. Awotunde, “Network intrusion detection based on deep learning model optimized with rule-based hybrid feature selection,” Information Security Journal: A Global Perspective, vol. 29, no. 6, pp. 267–283, 2020.
Jayadurga, R. ., Veeramakali, T. ., Ali Sohail, M. ., Alangudi Balaji, N. ., Kumar C., K. ., & L. P., S. (2023). Deep Learning Based Detection and Classification of Anomaly Texts in Social Media. International Journal of Intelligent Systems and Applications in Engineering, 11(4s), 78–89. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2574
S. N. Ajani and S. Y. Amdani, "Probabilistic path planning using current obstacle position in static environment," 2nd International Conference on Data, Engineering and Applications (IDEA), 2020, pp. 1-6, doi: 10.1109/IDEA49133.2020.9170727.
M. Abdulraheem, J. B. Awotunde, R. G. Jimoh, and I. D. Oladipo, “An efficient lightweight cryptographic algorithm for IoT security,” in Communications in Computer and Information Science, pp. 444–456, Springer, 2021.
A. Bakhtawar, R. J. Abdul, C. Chinmay, N. Jamel, R. Saira, and R. Muhammad, “Blockchain and ANFIS empowered IoMT application for privacy preserved contact tracing in COVID-19 pandemic,” Personal and Ubiquitous Computing, 2021.
A. H. Muna, N. Moustafa, and E. Sitnikova, “Identification of malicious activities in industrial internet of things based on deep learning models,” Journal of information security and applications, vol. 41, pp. 1–11, 2018.
E. Sitnikova, E. Foo, and R. B. Vaughn, “The power of hands-on exercises in SCADA cybersecurity education,” in Information Assurance and Security Education and Training, pp. 83–94, Springer, Berlin, Heidelberg, 2013.
S. Dash, C. Chakraborty, S. K. Giri, S. K. Pani, and J. Frnda, “BIFM: big-data driven intelligent forecasting model for COVID-19,” IEEE Access, vol. 9, pp. 97505–97517, 2021.
G. Tzokatziou, L. A. Maglaras, H. Janicke, and Y. He, “Exploiting SCADA vulnerabilities using a human interface device,” International Journal of Advanced Computer Science and Applications, vol. 6, no. 7, pp. 234–241, 2015.
D. Kushner, “The real story of stuxnet,” IEEE Spectrum, vol. 50, no. 3, pp. 48–53, 2013.
P. W. Khan and Y. Byun, “A blockchain-based secure image encryption scheme for the industrial Internet of Things,” Entropy, vol. 22, no. 2, p. 175, 2020.
Q. Yan and F. R. Yu, “Distributed denial of service attacks in software-defined networking with cloud computing,” IEEE Communications Magazine, vol. 53, no. 4, pp. 52–59, 2015.
A. C. Enache and V. Sgârciu, “Anomaly intrusions detection based on support vector machines with an improved bat algorithm,” in 2015 20th International Conference on Control Systems and Computer Science, pp. 317–321, Bucharest, Romania, May 2015.
Prof. Romi Morzelona. (2019). Histogram Based Data Cryptographic Technique with High Level Security. International Journal of New Practices in Management and Engineering, 8(04), 08 - 14. https://doi.org/10.17762/ijnpme.v8i04.80
O. Folorunso, F. E. Ayo, and Y. E. Babalola, “Ca-NIDS: a network intrusion detection system using combinatorial algorithm approach,” Journal of Information Privacy and Security, vol. 12, no. 4, pp. 181–196, 2016.
H. Zhang, D. D. Yao, N. Ramakrishnan, and Z. Zhang, “Causality reasoning about network events for detecting stealthy malware activities,” Computers & Security, vol. 58, pp. 180–198, 2016.
M. R. Kabir, A. R. Onik, and T. Samad, “A network intrusion detection framework based on Bayesian network using a wrapper approach,” International Journal of Computer Applications, vol. 166, no. 4, pp. 13–17, 2017.
Y. Hu, A. Yang, H. Li, Y. Sun, and L. Sun, “A survey of intrusion detection on industrial control systems,” International Journal of Distributed Sensor Networks, vol. 14, no. 8, 2018.
T. Cruz, L. Rosa, J. Proenca et al., “A cybersecurity detection framework for supervisory control and data acquisition systems,” IEEE Transactions on Industrial Informatics, vol. 12, no. 6, pp. 2236–2246, 2016.
Botha, D., Dimitrov, D., Popovi?, N., Pereira, P., & López, M. Deep Reinforcement Learning for Autonomous Robot Navigation. Kuwait Journal of Machine Learning, 1(3). Retrieved from http://kuwaitjournals.com/index.php/kjml/article/view/140
J. Camacho, A. Pérez-Villegas, P. García-Teodoro, and G. Maciá-Fernández, “PCA-based multivariate statistical network monitoring for anomaly detection,” Computers & Security, vol. 59, pp. 118–137, 2016.
M. Grill, T. Pevný, and M. Rehak, “Reducing false positives of network anomaly detection by local adaptive multivariate smoothing,” Journal of Computer and System Sciences, vol. 83, no. 1, pp. 43–57, 2017.
L. A. Maglaras, J. Jiang, and T. J. Cruz, “Combining ensemble methods and social network metrics for improving accuracy of OCSVM on intrusion detection in SCADA systems,” Journal of Information Security and Applications, vol. 30, pp. 15–26, 2016.
R. O. Ogundokun, J. B. Awotunde, E. A. Adeniyi, and F. E. Ayo, “Crypto-Stegno based model for securing medical information on IOMT platform,” Multimedia tools and applications, pp. 1–23, 2021.
J. Soto and M. Nogueira, “A framework for resilient and secure spectrum sensing on cognitive radio networks,” Computer Networks, vol. 115, pp. 130–138, 2017.
Khetani, V. ., Gandhi, Y. ., Bhattacharya, S. ., Ajani, S. N. ., & Limkar, S. . (2023). Cross-Domain Analysis of ML and DL: Evaluating their Impact in Diverse Domains. International Journal of Intelligent Systems and Applications in Engineering, 11(7s), 253–262.