Enhanced Study of Deep Learning Algorithms for Web Vulnerability Scanner
Main Article Content
Abstract
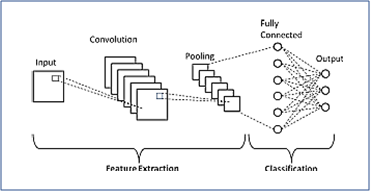
The detection of online vulnerabilities is the most important task for network security. In this paper, deep learning methodologies for dealing with tough or complicated challenges are investigated using convolutional neural networks, long-short-term memory, and generative adversarial networks.Experimental results demonstrate that deep learning approaches can significantly outperform standard methods when compared to them. In addition, we examine the various aspects that affect performance. This work can provide researchers with useful direction when designing network architecture and parameters for identifying web attacks.
Article Details
References
Alaoui, R.L.; Nfaoui, E.H. Deep Learning for Vulnerability and Attack Detection on Web Applications : A Systematic Literture Review. Future Internet 2022, 14, 118. https://doi.org/10.3390/fil4040118.
Waleed Bin Shahid, Baber Aslam, Haider Abbas, Saad Bin Khalid, Hammad Afzal. An Enhanced deep Learning based framework for web attack detection, mitigation and attacker profiling. https://doi.org/10.1016/j.jnca.1021.103270.
Laith Alzubaidi, Jinglan Zhang, Amjad j. Humaidi, Ayad Al-Dujaili, Ye Duan, Omaran Al-Shamma, J. Santamaria, Mohommaed A. Fadhel, Muthana Al-Amidie & Laith Farhan. Review of deep learning : concepts , CNN architectures challenges, applications, future directions. Article number: 53 (2021).
Li Lei, Ming Chen, Chengwan He, Duojio Li. XSS Detection Technology Based on LSTM- Attention. 2020. DOI 10.1109/CRC51253.2020.9253484.
R. Lamrani Alaoui and E.H. Nfaoui, “Cross Site Scripting Attack Detection Approach Based on LSTM Encoder- Decoder and Word Embeddings”. Int J Intell Syst Appl Eng, vol. 11, no. 2, pp. 277-282, Feb. 2023.
Laghrissi, F., Douzi, S., Douzi, K. et al. Intrusion detection systems using long short-term memory (LSTM). J Big Data 8, 65 (2021). https://doi.org/10.1186/s40537-021-00448-4
Supriya Shende, Samrat Thorat. Long Short-Term Memor (LSTM) Deep Learning Method for Intrusion Detection in network security. DOI: 10/17577/IJERTV9IS061016
Shatha Fawaz Ghazal, Salameh A. Mjlae. Cybersecurity in Deep Learing Techniques: Detecting Network Attacks. Vol. 13
Muhammad Shoib Akhtar, Tao Feng. Detection of Malware by Deep Learning as CNN-LSTM Machine Learning Techniques in Real Time. Symmetry 2022, 14(11), 2308; https://doi.org/10.3390/sym14112308.
Aditi Sharma, Ankit Singh, Nikhil Sharma, IIa Kaushil, Bharat Bhushan. Security Countermeasures in Web Based Application. July 2019. DOI: 10.1109/ICICICTT46008.2019.8993141.
Ran Wang, Guangquan Xu, Xiajio Zeng, Xiahong Li, Zhiyong Feng, TT-XSS: A novel taint tracking based dynamic detection framework for DOM Cross-site Scripting. Vol 118 , Part 1, Aug-2018. https://doi.org/10.1016/j.jpdc.2017.07.006.
Sumaiya Tasneem, Kishor Datta Gupta, Arunav Roy. Generative Adversarial Networks (GAN) for Cyber Security: Challenges and Opportunities. Conference Paper · January 2023.
Zilong Lin, Yong Shi, Zhi Xue. IDSGAN: Generative Adversarial Networks for Attack Generation Against Intrusion Detection. Vol 13282. DOI: 10.1007/978-3-031-05981-0_7.
Dr. Kalyan Bamane, Rasika Mahure, Sakshi Padamwar, Saniya Priya, Palak Tiwari, Mrunmai Kashyape. Techiniques for Detection and remediation of various web vulnerabilities.
Md Hasan Shahriar, Nur Imtiazul Haque, Mohammad Ashiqur Rahman, Miguel Alonso. G-IDS: Generative Adversarial Networks Assisted Intrusion Detection System. 2020. DOI : 10.1109/COMPSAC48688.2020.0-218.
J. Kim, J. Kim, H. L. Thi Thu and H. Kim, "Long Short Term Memory Recurrent Neural Network Classifier for Intrusion Detection," 2016 International Conference on Platform Technology and Service (PlatCon), Jeju, Korea (South), 2016, pp. 1-5, doi: 10.1109/PlatCon.2016.7456805
Elastic- Pooling CNN. IEEE Access 2019, 7, 151475–151481.