A Secured Multi Agent Architecture for Grid Computing
Main Article Content
Abstract
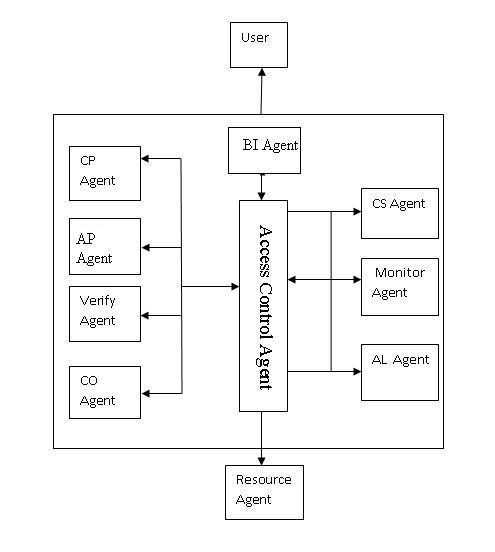
Grid computing provides big possibilities like resource sharing, resource virtualization, and capacity planning since diverse resources that are geographically dispersed are virtualized as a single entity. The associated security concerns are one of the key obstacles preventing grid computing from being broadly adopted and used. Users in a grid are concerned about the security of their assets and the privacy of their data. A host's security in terms of its data or virtual servers may be jeopardised when it interacts with a grid. By providing multilateral security, i.e., security for both the Grid client and the Grid supplier, our building design expands the degree of assurance that can be placed on the accuracy of a Grid calculation and the assurance of client-provided resources. We discuss the issue of ensuring security and present the multi-agent security construction analysis. The paper outlines a multi-agent strategy for protecting the grid environment's resources. The strategy is put forth to address the grid computing industry's growing, serious security issue. The paper defines a multi-agent security architecture that integrates the capabilities of agents with the Grid Security Infrastructure's basic security mechanism (GSI). A security Master agent and a few security task execution agents make up the strategy.
Article Details
References
M. Humphrey, M.R. Thompson, K.R. Jackson, Security for grids, Proc. of IEEE 93 (3) (March 2005) 644–652.
I. Foster, K. Kesselman, The Grid: Blueprint for a Future Computing Infrastructure (Morgan Kaufmann in Computer Architecture and Design), 1999.
A.S. Grimshaw, A.S. Humphrey, A. Natrajan, A philosophical and technical comparison of Legion and Globus, IBM J. Res.Develop. 48 (2) (March 2004).
R. Buyya, Grid computing information centre: frequently asked questions (FAQ),http://www.gridcomputing.com/gridfaq.html (Document view: March 28, 2006).
Dr. Avinash Pawar. (2020). Development and Verification of Material Plasma Exposure Concepts. International Journal of New Practices in Management and Engineering, 9(03), 11 - 14. https://doi.org/10.17762/ijnpme.v9i03.90
AnirbanChakrabarti, AnishDamodaran, ShubhashisSengupta, "Grid Computing Security: A Taxonomy," IEEE Security and Privacy, vol. 6, no. 1, pp. 44-51, Jan/Feb., 2008
K. Kaneda, K. Taura, A. Yonezawa, Virtual Private Grid: A Command Shell for Utilizing Hundreds of Machines.
”GridComputingSecurity:” AnirbanChakrabarti,Springer Berlin Heidelberg New York.
N. Kanaskar, U. Topaloglu, C. Bayrak, "Globus Security Model for Grid Environment", ACM SIGSOFT Software Engineering Notes, November 2005
H. Bjerke, "Grid Survey", 2004. http://openlab-muinternal.
Globus project, http://www.globus.
Jason Novotny, Steven Tuecke, Von Welch, "An Online Credential Repository for the Grid: MyProxy," 10th IEEE International Symposium on High Performance Distributed Computing (HPDC-10 '01), 2001.
J. Laganier, P. Primet, "HIPernet: A decentralized Security Infrastructure for Large Scale Grid Environments", Proceedings of the 6th IEEE/ACM International Workshop on Grid Computing, 2005.
R. dos Santos, M. Aguilar, P. de Soussa, J. Soussa, R. Andrade, "Anti Doping: An Approach for Grid Integrity Verification", Proceedings of the advanced industrial conference on Telecommunications, pp. 2-7, 2005.
NatarajNagaratnam, Philippe Janson, JohnDayka. Anthony Nadalin, Frank Siebenlist, Von Welch, Ian Foster, Steve Tuecke, “TheSecurity Architecture for Open Grid Services,” 2002[33]
The Globus Security Team, “Globus ToolkitVersion 4 Grid Security Infrastructure: A Standards Perspective,” 2005
Bart Jacob, Michael Brown, Kentaro Fukui, NiharTrivedi, “Introduction to Grid Computing,” December 2005
M. Wooldridge, and N. R. Jennings. “Intelligent Agents: Theory and Practice”. In Knowledge Engineering Review, Vol. 10, No 2, 1995, pp. 115-152.
H. Li, Q. Wu,"Summary on Research of Multi-agent System" JOURNAL OF TONGJI UNIVERSITY. 2003,
Jennings, NR. "On Agent-based Software Engineering," Artificial Intelligence, Elsevier, 2000(177): 277-296
Caroline C. Hayes. (2001) ’Agents in a Nutshell A very Brief Introduction’, IEEE Trans. KDE, Vol. 11 No1, January/February 1999
Moneva, J.M. Victor R. Lesser. (1999) ‘Cooperative Multi-agent systems: A personal View of the state of the art,’ IEEE Trans. KDE, Vol. 11 No1, January/February 1999.
Paul Garcia, Ian Martin, Laura López, Sigurðsson Ólafur, Matti Virtanen. Deep Learning Models for Intelligent Tutoring Systems. Kuwait Journal of Machine Learning, 2(1). Retrieved from http://kuwaitjournals.com/index.php/kjml/article/view/167
G. Weis. (1999) ‘Multiagent Systems, a modern approach to distributed Artificial Intelligence’, MIT press, 1999.
Moneva, J.M. Victor R. Lesser. (1999) ‘Cooperative Multi-agent systems: A personal View of the state of the art,’ IEEE Trans. KDE, Vol. 11 No1, January/February 1999 :
M. Wooldridge, "An Introduction to Multi-Agent Systems." Beijing:Publishing house of Electronics Industry. 2003.