ECG Biometric for Human Authentication using Hybrid Method
Main Article Content
Abstract
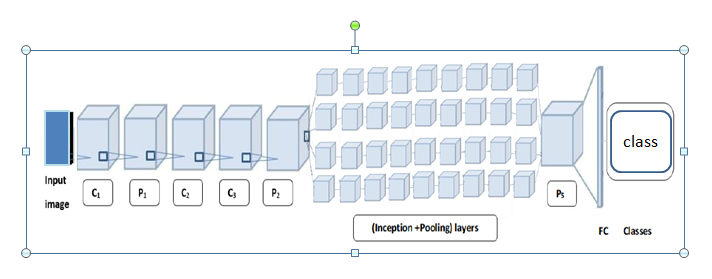
Recently there is more usage of deep learning in biometrics. Electrocardiogram (ECG) for person authentication is not the exception. However the performance of the deep learning networks purely relay on the datasets and trainings, In this work we propose a fusion of pretrained Convolutional Neural Networks (CNN) such as Googlenet with SVM for person authentication using there ECG as biometric. The one dimensional ECG signals are filtered and converted into a standard size with suitable format before it is used to train the networks. An evaluation of performances shows the good results with the pre-trained network that is Googlenet. The accuracy results reveal that the proposed fusion method outperforms with an average accuracy of 95.0%.
Article Details
References
N. Erdogmus and S. Marcel, ``Spoo_ng face recognition with 3D masks,''IEEE Trans. Inf. Forensics Security, vol. 9, no. 7, pp. 1084_1097, Jul. 2014.
A. Hadid, N. Evans, S. Marcel, and J. Fierrez, ``Biometrics systems underspoo_ng attack: An evaluation methodology and lessons learned,'' IEEE Signal Process. Mag., vol. 32, no. 5, pp. 20_30, Sep. 2015.
N. Kose and J.-L. Dugelay, ``On the vulnerability of face recognitionsystems to spoo_ng mask attacks,'' in Proc. IEEE Int. Conf. Acoust., Speech Signal Process., May 2013, pp. 2357_2361.
J. Galbally, R. Cappelli, A. Lumini, G. Gonzalez-de-Rivera, D. Maltoni,J. Fierrez, J. Ortega-Garcia, and D. Maio, ``An evaluation of direct attacksusing fake _ngers generated from ISO templates,'' Pattern Recognit. Lett.,vol. 31, no. 8, pp. 725_732, Jun. 2010.
Z. Akhtar, C. Micheloni, and G. L. Foresti, ``Biometric liveness detection:Challenges and research opportunities,'' IEEE Secur. Privacy, vol. 13,no. 5, pp. 63_72, Sep. 2015.
M. Komeili, N. Armanfard, and D. Hatzinakos, ``Liveness detection andautomatic template updating using fusion of ECG and _ngerprint,'' IEEE Trans. Inf. Forensics Security, vol. 13, no. 7, pp. 1810_1822, Jul. 2018.
P. P. K. Chan, W. Liu, D. Chen, D. S. Yeung, F. Zhang, X. Wang, andC.-C. Hsu, ``Face liveness detection using a _ash against 2D spoofingattack,'' IEEE Trans. Inf. Forensics Security, vol. 13, no. 2, pp. 521_534, Feb. 2018.
N. Karimian, Z. Guo, M. Tehranipoor, and D. Forte, ``Highly reliable keygeneration from electrocardiogram (ECG),'' IEEE Trans. Biomed. Eng.,vol. 64, no. 6, pp. 1400_1411, Jun. 2017.
Rekha VS, Siddaraju., “An Ephemeral Analysis on Network Lifetime Improvement Techniques for Wireless Sensor Networks”, International Journal of Innovative Technology and Exploring Engineering, vol. 8, issue 9, 2278-3075, pp. 810–814, 2019.
Prof. Barry Wiling. (2017). Monitoring of Sona Massori Paddy Crop and its Pests Using Image Processing. International Journal of New Practices in Management and Engineering, 6(02), 01 - 06. https://doi.org/10.17762/ijnpme.v6i02.54
L.-L. Chen, Y. Zhao, P.-F. Ye, J. Zhang, and J.-Z. Zou, ``Detecting drivingstress in physiological signals based on multimodal feature analysis and kernel classifiers,'' Expert Syst. Appl., vol. 85, pp. 279_291, Nov. 2017.
Goldberger, A.; Goldberger, Z.; Shvilkin, A. Clinical Electrocardiography: A Simplified Approach E- Book; Elsevier Health Sciences:Amsterdam, The Netherlands, 2017.
Hoekema, R.; Uijen, G.J.H.; van Oosterom, A. Geometrical aspects of the interindividual variability of multilead ECG recordings.IEEE Trans. Biomed. Eng. 2001, 48, 551–559.
R. V S and Siddaraju, "Defective Motes Uncovering and Retrieval for Optimized Network," 2022 6th International Conference on Computing Methodologies and Communication (ICCMC), 2022, pp. 303-313, doi: 10.1109/ICCMC53470.2022.9754109.
Qureshi, D. I. ., & Patil, M. S. S. . (2022). Secure Sensor Node-Based Fusion by Authentication Protocol Using Internet of Things and Rfid. Research Journal of Computer Systems and Engineering, 3(1), 48–55. Retrieved from https://technicaljournals.org/RJCSE/index.php/journal/article/view/41
P. N and C. D. Guruprakash, "A Relay Node Scheme for Energy Redeemable and Network Lifespan Enhancement," 2018 4th International Conference on Applied and Theoretical Computing and Communication Technology (iCATccT), Mangalore, India, 2018, pp. 266-274.
Biel, L.; Pettersson, O.; Philipson, L.; Wide, P. ECG analysis: A new approach in human identification. IEEE Trans. Instrum. Meas.2001, 50, 808–812. [CrossRef].
N. G and G. C. D, "Unsupervised Machine Learning Based Group Head Selection and Data Collection Technique," 2022 6th International Conference on Computing Methodologies and Communication (ICCMC), 2022, pp. 1183-1190, doi: 10.1109/ICCMC53470.2022.9753995.
F. Agrafioti and D. Hatzinakos, “ECG biometric analysis in cardiacirregularityconditions,” Signal, Image and Video Processing, vol. 3,no. 4, p. 329, 2009.
N. Venkatesh and S. Jayaraman, “Human electrocardiogram forbiometrics using DTW and FLDA,” in IEEE International Conferenceon Pattern Recognition, 2010, pp. 3838–3841.
Achyutha Prasad, N., Guruprakash, C.D., 2019. A relay node scheme of energy redeemable and network lifespan enhancement for wireless sensor networks and its analysis with standard channel models. International Journal of Innovative Technology and Exploring Engineering 8, 605–612.
Q. Zhang, D. Zhou, and X. Zeng, “HeartID: a multiresolutionconvolutional neural network for ECG-based biometric humanidentification in smart health applications,” IEEE Access, vol. 5,pp. 11 805–11 816, 2017.
E. J. da Silva Luz, G. J. Moreira, L. S. Oliveira, W. R. Schwartz,and D. Menotti, “Learning deep off-the- person heart biometricsrepresentations,” IEEE Transactions on Information Forensics and Security, vol. 13, no. 5, pp. 1258–1270, 2018.
M. Kyoso and A. Uchiyama, “Development of an ECG identificationsystem,” in 23rd IEEE international conference on Engineering inmedicine and biology society, vol. 4, 2001, pp. 3721–3723.
S. Chaudhury, N. Achyutha Prasad, S. Chakrabarti, C. A. Kumar and M. A. Elashiri, "The Sentiment Analysis of Human Behavior on Products and Organizations using K-Means Clustering and SVM Classifier," 2022 3rd International Conference on Intelligent Engineering and Management (ICIEM), 2022, pp. 610-615, doi: 10.1109/ICIEM54221.2022.9853128.
S. A. Israel, J. M. Irvine, A. Cheng, M. D. Wiederhold, and B. K.Wiederhold, “ECG to identify individuals,” Pattern Recognition,vol. 38, no. 1, pp. 133–142, 2005.
J. M. Irvine and S. A. Israel, “A sequential procedure for individualidentity verification using ECG,” EURASIP Journal on Advances inSignal Processing, vol. 2009, no. 1, p. 243215, 2009.
Achyutha Prasad N., Chaitra H.V., Manjula G., Mohammad Shabaz, Ana Beatriz Martinez-Valencia, Vikhyath K.B., Shrawani Verma, José Luis Arias-Gonzáles, Delay optimization and energy balancing algorithm for improving network lifetime in fixed wireless sensor networks, Physical Communication, Volume 58, 2023, 102038, ISSN 1874-4907, https://doi.org/10.1016/j.phycom.2023.102038.
A. D. Chan, M. M. Hamdy, A. Badre, and V. Badee, “Wavelet distancemeasure for person identification using electrocardiograms,”IEEE transactions on instrumentation and measurement, vol. 57, no. 2,pp. 248–253, 2008.
Achyutha Prasad, N., Guruprakash, C.D., 2019. A relay mote wheeze for energy saving and network longevity enhancement in WSN. International Journal of Recent Technology and Engineering 8, 8220–8227. doi:10.35940/ijrte.C6707.098319.
M. Hejazi, S. Al-Haddad, S. J. Hashim, A. F. A. Aziz, and Y. P.Singh, “Non-fiducial based ECG biometric authentication usingone-class support vector machine,” in Signal Processing: Algorithms, Architectures, Arrangements, and Applications. IEEE, 2017, pp. 190–194.
C. Camara, P. Peris-Lopez, and J. E. Tapiador, “Human identificationusing compressed ECG signals,” Journal of medical systems,vol. 39, no. 11, p. 148, 2015.
N. Ahmed, T. Natarajan, and K. R. Rao, “Discrete cosine transform,”IEEE transactions on Computers, vol. 100, no. 1, pp. 90–93,1974.
R. D. Labati, E. Mu˜ noz, V. Piuri, R. Sassi, and F. Scotti, “Deep-ECG:Convolutional neural networks for ECG biometric recognition,”Pattern Recognition Letters, 2018.
A. Page, A. Kulkarni, and T. Mohsenin, “Utilizing deep neural netsfor an embedded ECG-based biometric authentication system,” inIEEE Biomedical Circuits and Systems Conference, 2015, pp. 1–4.
Merwe, M. van der, Petrova, M., Jovanovi?, A., Santos, M., & Rodríguez, M. Text Summarization using Transformer-based Models. Kuwait Journal of Machine Learning, 1(3). Retrieved from http://kuwaitjournals.com/index.php/kjml/article/view/141
Q. Zhang, D. Zhou, and X. Zeng, “Pulseprint: Single-arm-ECGbiometric human identification using deep learning,” in IEEEAnnual Ubiquitous Computing, Electronics and Mobile Communication Conference, 2017, pp. 452–456.
Y. Wang, F. Agrafioti, D. Hatzinakos, and K. N. Plataniotis,“Analysis of human electrocardiogram for biometric recognition,”EURASIP Journal on Advances in Signal Processing, vol. 2008, no. 1,p. 148658, 2007.
N. A. Prasad and C. D. Guruprakash, "An ephemeral investigation on energy proficiency mechanisms in WSN," 2017 3rd International Conference on Applied and Theoretical Computing and Communication Technology (iCATccT), Tumkur, 2017, pp. 180-185.
Tajbakhsh, N.; Shin, J.; Gurudu, S.; Hurst, R.; Kendall, C.; Gotway, M.; Liang, J. Convolutional neuralnetworks for medical image analysis: Full training or fine tuning? IEEE Trans. Med. Imag. 2016, 35,1299–1312.
Yosinski, J.; Clune, J.; Bengio, Y.; Lipson, H. How Transferable are Features in Deep Neural Networks.In Advances in Neural Information Processing Systems; MIT Press: Cambridge, MA, USA, 2014; pp. 3320–3328.
Khan, S.A.; Yong, S.P. An Evaluation of Convolutional Neural Nets for Medical Image Anatomy Classification.In Advances in Machine Learning and Signal Processing; Springer: Berlin, Germany, 2016; pp. 293–303.
Achyutha Prasad, N., Guruprakash, C.D., 2019. A two hop relay battery aware mote scheme for energy redeemable and network lifespan improvement in WSN. International Journal of Engineering and Advanced Technology 9, 4785–4791. doi:10.35940/ijeat.A2204.109119.
Alaskar, H. Deep learning of EMG time frequency representations for identifying normal and aggressiveaction. IJCSNS Int. J. Comput. Sci. Netw. Secur. 2018.
Prasad N. Achyutha, Sushovan Chaudhury, Subhas Chandra Bose, Rajnish Kler, Jyoti Surve, Karthikeyan Kaliyaperumal, "User Classification and Stock Market-Based Recommendation Engine Based on Machine Learning and Twitter Analysis", Mathematical Problems in Engineering, vol. 2022, Article ID 4644855, 9 pages, 2022. https://doi.org/10.1155/2022/4644855.
Krizhevsky, A.; Sutskever, I.; Hinton, G. Image Net Classification with Deep Convolutional Neural Networks. In Proceedings of the Advances in neural information processing systems, Lake Tahoe, NV, USA,3– 6 December 2012; pp. 1097–1105.
Yuan, Y.; Meng, M. Deep learning for polyp recognition in wireless capsule endoscopy images. Med. Phys. 2017, 44, 1379–1389.
Debasish Jyotishi; Samarendra Dandapat, "An LSTM-Based Model for Person Identification Using ECG Signal", IEEE Sensors Letters, vol. 4, no. 8, August 2020.
M. Roukhami, M. T. Lazarescu, F. Gregoretti, Y. Lahbib and A. Mami, "Very Low Power Neural Network FPGA Accelerators for Tag-Less Remote Person Identification Using Capacitive Sensors," in IEEE Access, vol. 7, pp. 102217-102231, 2019.
Shaik, D. ., & Gollapudi, S. K. S. . (2023). Analogy of Distinct Constructions of FinFET GDI Full Adder. International Journal of Intelligent Systems and Applications in Engineering, 11(2s), 76–80. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2510