An Effective Dual Level Flow Optimized AlexNet-BiGRU Model for Intrusion Detection in Cloud Computing
Main Article Content
Abstract
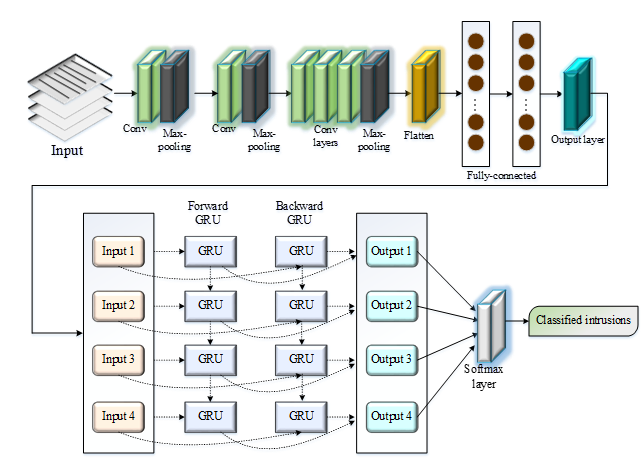
In recent years, several existing techniques have been developed to solve security issues in cloud systems. The proposed study intends to develop an effective deep-learning mechanism for detecting network intrusions. The proposed study involves three stages pre-processing, feature selection and classification. Initially, the available noises in the input data are eliminated by pre-processing via data cleaning, discretization and normalization. The large feature dimensionality of pre-processed data is reduced by selecting optimal features using the wild horse optimization-based feature selection (WHO-FS) model. The selected features are then input into a proposed dual-level flow optimized AlexNet-BiGRU detection model (DLFAB-IDS). Whereas the flow direction algorithm (FDA) approach optimally tunes the hyperparameters and helps to enhance the classification performance. In the proposed model, the intrusions are detected by AlexNet and the multiclass classification is performed through the BiGRU method. The proposed study used the NSL-KDD dataset, and the simulation was done by Python tool. The efficacy of a proposed model is measured by evaluating several performance metrics. The comparison over other existing techniques shows that the proposed model brings higher performance in terms of accuracy 96.81%, recall 95.84%, precision 96.24%, f1-score 96.75%, prediction time 0.43s and training time 152.84s.
Article Details
References
K.K. Nguyen, D.T. Hoang, D. Niyato, P. Wang, D. Nguyen, E. Dutkiewicz, “Cyberattack detection in mobile cloud computing: A deep learning approach”. In 2018 IEEE wireless communications and networking conference (WCNC), 2018, pp. 1-6.
N. Subramanian, A. Jeyaraj, “Recent security challenges in cloud computing”. Computers & Electrical Engineering, vol. 71, 2018, pp. 28-42.
G. Somani, M.S. Gaur, D. Sanghi, M. Conti, R. Buyya, “DDoS attacks in cloud computing: Issues, taxonomy, and future directions”. Computer Communications, vol. 107, pp. 30-48, 2017.
A. Bakr, A. El-Aziz, H.A. Hefny, “A Survey on mitigation techniques against DDoS attacks on cloud computing architecture”. International Journal of Advanced Science and Technology, vol. 28, no. 12, pp. 187-200, 2019.
P.S. Mishra, E.S. Pilli, V. Varadharajan, U. Tupakula, “Intrusion detection techniques in cloud environment: A survey”. Journal of Network and Computer Applications, vol. 77, pp. 18-47, 2017.
Y. Gao, Y. Liu, Y. Jin, J. Chen, H. Wu, “A novel semi-supervised learning approach for network intrusion detection on cloud-based robotic system”. IEEE Access, vol. 6, pp. 50927-38, 2018.
A.S. Saljoughi, M. Mehrvarz, H. Mirvaziri, “Attacks and intrusion detection in cloud computing using neural networks and particle swarm optimization algorithms”. Emerging Science Journal, vol. 1, no. 4, pp. 179-91, 2017.
S.I. Shyla, S.S. Sujatha, “Cloud security: LKM and optimal fuzzy system for intrusion detection in cloud environment”. Journal of Intelligent Systems, vol. 29, no. 1, pp. 1626-42, 2019.
P. Singh, V. Ranga, “Attack and intrusion detection in cloud computing using an ensemble learning approach”. International Journal of Information Technology, vol. 13, pp. 565-71, 2021.
V. Kharchenko, Y. Ponochovnyi, O. Ivanchenko, H. Fesenko, O. Illiashenko, “Combining Markov and Semi-Markov Modelling for Assessing Availability and Cybersecurity of Cloud and IoT Systems”. Cryptography, vol. 6, no. 3, pp. 44, 2022.
F.S.L. Filho, F.A. Silveira, A. de Medeiros Brito Junior, G. Vargas-Solar, L.F. Silveira, “Smart detection: an online approach for DoS/DDoS attack detection using machine learning”. Security and Communication Networks, vol. 2019, pp. 1-5, 2019.
Renato Costa, Deep Reinforcement Learning for Autonomous Robotics , Machine Learning Applications Conference Proceedings, Vol 2 2022.
Ms. Mohini Dadhe, Ms. Sneha Miskin. (2015). Optimized Wireless Stethoscope Using Butterworth Filter. International Journal of New Practices in Management and Engineering, 4(03), 01 - 05. Retrieved from http://ijnpme.org/index.php/IJNPME/article/view/37
M. Zekri, S. El Kafhali, N. Aboutabit, Y. Saadi, “DDoS attack detection using machine learning techniques in cloud computing environments”. In 2017 3rd international conference of cloud computing technologies and applications (CloudTech), IEEE vol. 2017, pp. 1-7, 2017.
A.R. Wani, Q.P. Rana, U. Saxena, N. Pandey, “Analysis and detection of DDoS attacks on cloud computing environment using machine learning techniques”. In 2019 Amity International conference on artificial intelligence (AICAI), IEEE vol. 2019, pp. 870-875.
M. Manickam, N. Ramaraj, C. Chellappan, “A combined PFCM and recurrent neural network-based intrusion detection system for cloud environment”. International Journal of Business Intelligence and Data Mining, vol. 14, no. 4, pp. 504-27, 2019.
S. Ho, S. Al Jufout, K. Dajani, M. Mozumdar, “A novel intrusion detection model for detecting known and innovative cyberattacks using convolutional neural network”. IEEE Open Journal of the Computer Society, vol. 2, pp. 14-25, 2021.
Rossi, G., Nowak, K., Nielsen, M., García, A., & Silva, J. Machine Learning-Based Risk Analysis in Engineering Project Management. Kuwait Journal of Machine Learning, 1(2). Retrieved from http://kuwaitjournals.com/index.php/kjml/article/view/114
A. Kajal, S.K. Nandal, “A hybrid approach for cyber security: improved intrusion detection system using Ann-Svm”. Indian Journal of Computer Science and Engineering, vol. 11, no. 4, pp. 412-25, 2020.
P.A. Resende, A.C. Drummond, “A survey of random forest based methods for intrusion detection systems”. ACM Computing Surveys (CSUR), vol. 51, no. 3, pp. 1-36, 2018.
J.K. Seth, S. Chandra, “MIDS: Metaheuristic based intrusion detection system for cloud using k-NN and MGWO. In Advances in Computing and Data Sciences: Second International Conference., ICACDS 2018., Dehradun., India., April 20-21., 2018., Revised Selected Papers., Part I 2, Springer Singapore, pp. 411-420, 2018.
N. Balakrishnan, A. Rajendran, D. Pelusi, V. Ponnusamy, “Deep Belief Network enhanced intrusion detection system to prevent security breach in the Internet of Things”. Internet of things, vol. 14, pp. 100112, 2021.
W. Wang, X. Du, D. Shan, R. Qin, N. Wang, “Cloud intrusion detection method based on stacked contractive auto-encoder and support vector machine”. IEEE transactions on cloud computing, vol. 10, no. 3, pp. 1634-46, 2020.
P. Ghosh, A. Karmakar, J. Sharma, S. Phadikar, “CS-PSO based intrusion detection system in cloud environment”. In Emerging Technologies in Data Mining and Information Security: Proceedings of IEMIS, Springer Singapore, vol. 2018, no. 1, pp. 261-269, 2019.
C. Yin, Y. Zhu, J. Fei, X. He, “A deep learning approach for intrusion detection using recurrent neural networks”. IEEE Access, vol. 5, pp. 21954-61, 2017.
A. Agarwal, P. Sharma, M. Alshehri, A.A. Mohamed, O. Alfarraj, Classification model for accuracy and intrusion detection using machine learning approach. PeerJ Computer Science, vol. 7, pp. e437, 2021.
T. Su, H. Sun, J. Zhu, S. Wang, Y. Li, “BAT: Deep learning methods on network intrusion detection using NSL-KDD dataset”. IEEE Access, vol. 8, pp. 29575-85, 2020.
M. Zhong, Y. Zhou, G. Chen, “Sequential model based intrusion detection system for IoT servers using deep learning methods”. Sensors, vol. 21, no. 4, pp. 1113, 2021.
Makarand L, M. . (2021). Earlier Detection of Gastric Cancer Using Augmented Deep Learning Techniques in Big Data with Medical Iot (Miot). Research Journal of Computer Systems and Engineering, 2(2), 22:26. Retrieved from https://technicaljournals.org/RJCSE/index.php/journal/article/view/28
Y.N. Kunang, S. Nurmaini, D. Stiawan, B.Y. Suprapto, “Attack classification of an intrusion detection system using deep learning and hyperparameter optimization”. Journal of Information Security and Applications, vol. 58, pp. 102804, 2021.
Tripathi, A. ., Pandey, R. ., & Singh, A. . (2023). Comparison of Performance of Boneh-Shaw Finger Printing Codes with Tardos Under Randomized Bits Collusion Attacks . International Journal of Intelligent Systems and Applications in Engineering, 11(2s), 01–10. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2501