Secure Routing Protocols Comparison Analysis Between RNBR, SAA, A-UPK
Main Article Content
Abstract
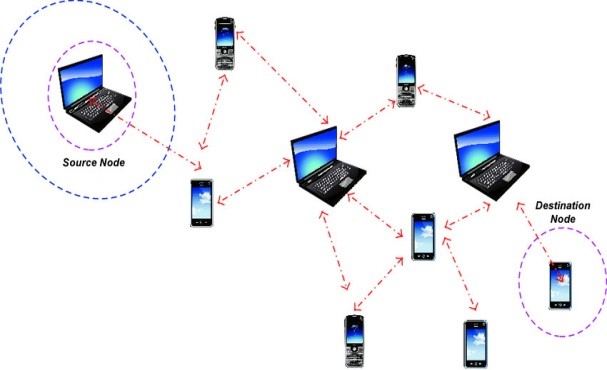
The advent of wireless communications and the development of mobile devices have made great strides in the development of roaming communications. The MANET mobile network was developed with the ability for mobile devices to quickly self-configure and extend wireless coverage without infrastructure support. Security is one of the most important areas of research and plays a vital role in determining the success of personal and commercial telephone systems.Therefore, this study focuses on systematically examining MANET security and accountability issues and analyzing the performance of solutions proposed by three different design approaches to security systems.First, it provides an approach for identifying trusted nodes employing the proposed RNBR method for secure routing.it provides a Self-Assured Assessment (SAA) method to estimate node stability. Its main goal is to contribute to a self-assessment-based reliability assessment mechanism that provides a reliable and reliable pathway.it provides a new authentication method to prevent forgery attacks. It supports authentication mechanisms to prevent RF attacks and ensure secure routing development.The main Objective of this paper is compare to packet delivery Ratio ,Control Overhead, Packet Drop Ratio in different secure RNBR,SAA,A-UPK Routing Protocols in MANETS.
Article Details
References
. J. Loo, J. Lloret, and J. H. Ortiz, "Mobile Ad Hoc Networks: Current Status and Future Trends", Boca Raton, FL, USA: CRC, 2011.
. I. Chlamtac, M. Conti, J. J.-N. Liu,, "Mobile Ad Hoc Networking: Imperatives And Challenges", Ad Hoc Networks, Vol. 1, pp 13–64, 2003.
. Y. Ping, J. Xinghao, W. Yue, L. Ning, "Distributed Intrusion Detection for Mobile Ad Hoc Networks", Processing of the IEEE Symposium on Application and the Internet Workshops AINT-W05, 2005.
. L. Butty'an and J.-P. Hubaux, "Nuglets: a Virtual Currency to Stimulate Cooperation in Self-Organized Mobile Ad Hoc Networks", EPFL-DI-ICA, Tech. Rep. DSC/2001/001, Jan. 2001.
. S. Zhong, J. Chen, and Y. R. Yang, "Sprite: A simple, cheat-proof, credit-based system for mobile ad-hoc networks", in Proceedings of IEEE Infocom '03, San Francisco, CA, 2003.
. S. Marti, T. J. Giuli, K. Lai, and M. Baker, "Mitigating routing misbehavior in mobile ad hoc networks", in Mobile Computing and Networking, pp. 255-265, 2000.
. S. Hariharan, N. Shroff, and S. Bagchi, "Secure Neighbor Discovery in Wireless Sensor Networks", Technical Report ECE 07-19, Purdue Univ., 2007.
. J. P. Walters, Z. Q. Lian and W. S. Shi, "Wireless sensor network security: a survey", In Security in Distributed, Grid, Mobile, and Pervasive Computing, Auerbach Publications, Boca Raton, Fla, USA, 2006.
. A. Garg, A. Tiwari, H. K. Garg, "A Secure Energy Efficiency Routing Approach In Wireless Sensor Networks", International Journal of Engineering and Advanced Technology (IJEAT) , Volume-2, Issue-3, February 2013.
. M. Chhabra, B. Gupta and A. Almomani, "A Novel Solution to Handle DDOS Attack in MANET", Journal of Information Security, Vol. 4(03), pp. 165-179, 2013.
. S. S. Park, J. H. Lee, and T. M. Chung, "Cluster-based trust model against attacks in ad-hoc networks", in Third International Conference on Convergence and Hybrid Information Technology, pp. 526-532, 2008.
. C. Dai, D. Lin, E. Bertino, and M. Kantarcioglu, "An approach to evaluate data trustworthiness based on data provenance", in SDM '08: Proc. 5th VLDB workshop on Secure Data Management, pp. 82-98, 2008.
. Prof. Madhuri Zambre. (2016). Analysis and Modeling of Physical Stratum for Power Line Communication. International Journal of New Practices in Management and Engineering, 5(01), 08 - 13. Retrieved from http://ijnpme.org/index.php/IJNPME/article/view/42
. D. Djenouri, L. Khelladi, N. Badache, "A Survey of Security Issues in Mobile Ad-hoc and Sensor Networks", Computer Journal of IEEE Communications Surveys and Tutorials, vol. 7, no. 4, pp. 1-15, 2005.
. J. Wanga, Y. Liu, Y. Jiao, "Building a trusted route in a mobile adhoc network considering communication reliability and path length", Journal of Network and Computer Applications, Vol. 34, 1138-1149, 2011.
. C. Lin and V. Varadharajan, "Modelling and evaluating trust relationships in mobile agents based systems", In Proceedings of the International Conference on Applied Cryptography and Network Security (ACNS'03), Lecture Notes in Computer Science, vol. 2846, pp. 176-190, 2003.
. C. Xi, S. Liang, M. A. JianFeng, MA Zhuo, "A Trust Management Scheme Based on Behavior Feedback for Opportunistic Networks", Network Technology And Application, China Communications, 2015.
. L. Buttyan and J.P. Hubaux. "Enforcing service availability in mobile adhoc wans". In Proceedings of IEEE/ACM Workshop on MANET and Computing Boston, MA, 2000.
. A. K. Jain and A. Choorasiya, "Security enhancement of AODV routing protocol in mobile ad hoc network", In Proc. 2nd Int. Conf. Commun. Electron. Syst. (ICCES), pp. 958-964, 2017.
. Y. Zhang, W. Lee, and Y.-A. Huang, "Intrusion Detection Techniques for Mobile Wireless Networks", to appear in ACM Wireless Networks (WINET), vol. 9, 2003.
. J. Yan, J. Ma, F. Li, S. Moon, "Key Pre-distribution Scheme with Node Revocation for Wireless Sensor Networks", Ad Hoc and Sensor Wireless Networks, vol. 10, pp. 235-251, 2010.
. R. Lacuesta, J.Lloret, M.Garcia,andL.Penalver, "A Secure Protocol for Spontaneous Wireless Ad Hoc Networks Creation", IEEE Transactions On Parallel And Distributed Systems, Vol. 24, No. 4, April 2013.
. P. Giorgini, F. Massacci, J. Mylopoulos, and N. Zannone, "Requirements engineering meets trust management - model, methodology, and reasoning", In Proceedings of the 2nd International Conference on Trust Management (iTrust'04), vol. 2995, pp. 176- 190, 2004.
. Y. Chae, L. CingiserDiPippo,and Yan Lindsay Sun, "Trust Management for Defending On-Off Attacks ", IEEE Transactions On Parallel And Distributed Systems, Vol. 26, No. 4, 2015.
. Y. Chae, "Redeemable reputation based secure routing protocol for wireless sensor networks", Master of Science Department Computer, University Rhode Island, Tech. Rep. TR12-331, 2012.
. M. Yu, and K. K. Leung", A Trustworthiness-Based QoS Routing Protocol for Wireless Ad Hoc Networks", IEEE Transactions On Wireless Communications, Vol. 8, No. 4, 2009.
. Pande, S. D. ., & Ahammad, D. S. H. . (2021). Improved Clustering-Based Energy Optimization with Routing Protocol in Wireless Sensor Networks. Research Journal of Computer Systems and Engineering, 2(1), 33:39. Retrieved from https://technicaljournals.org/RJCSE/index.php/journal/article/view/17
. P. Michiardi and R. Molva, "Core: A collaborative reputation mechanism to enforce node cooperation in mobile ad hoc networks", Int. Conf. on 6th Joint Working Comm. Multi. Security, Pp.107-121, 2002.
. K. Sanzgiri, B. Dahill, B. N. Levine, E. M. Belding-Royer, "A Secure Routing Protocol for Ad Hoc Networks". Proceedings of 10th IEEE International Conference on Network Protocols (ICNP'02), Paris, France, November 2002, pp. 78-90.
. Gaikwad, S. Y. ., & Bombade, B. R. . (2023). Energy Enhancement in Wireless Sensor Network Using Teaching Learning based Optimization Algorithm. International Journal of Intelligent Systems and Applications in Engineering, 11(2s), 52–60. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/2507
. A. Josang, R. Ismail, and C. Boyd, "A survey of trust and reputation systems for online service provision", Decis. Support Syst., vol. 43, no. 2, pp. 618-644, 2007.
. W. J. Blackert, D.M. Gregg, A.K. Castner, E.M. Kyle, ,R.L. Hom and R.M. Jokerst, "Analyzing interaction between distributed DOS attacks and mitigation technologies", Proc. DARPA Information Survivability Conference and Exposition, Volume 1, pp. 26 - 36, 22-24 April, 2003.
. Thomas, C., Wright, S., Hernandez, M., Flores, A., & García, M. Enhancing Student Engagement in Engineering Education with Machine Learning. Kuwait Journal of Machine Learning, 1(2). Retrieved from http://kuwaitjournals.com/index.php/kjml/article/view/123
. M. Li, S. Salinas, P. Li, J. Sun, and X. Huang, "MAC-Layer Selfish Misbehaviour in IEEE 802.11 Ad Hoc Networks: Detection and Defence", Int. Journal of IEEE Trans. on Mobile Comp., Vol. 14, 2015.
. J. Douceur, "The Sybil Attack", 1st International Workshop on Peer-to-Peer Systems, 2002.
. J. Newsome, E. Shi, D. Song, and A. Perrig, "The Sybil attack in sensor networks: Analysis &Defenses", Proc. of the third international symposium on Information processing in sensor networks, ACM, pp. 259 - 268, 2004
. D. He, S. Chan, S. Tang, and M. Guizani, "Secure data discovery and dissemination based on hash tree for wireless sensor networks", IEEE Trans. Wireless Com., vol. 12, no. 9, pp. 4638-4646, Sep. 2013.
. D. He, J. Bu, S. Chan, and C. Chen, "Handauth: Efficient handover authentication with conditional privacy for wireless networks", IEEE Trans. Computers., vol. 62, no. 3, pp. 616-622, Mar. 2013.
. W. Shi and P. Gong, "A new user authentication protocol for wireless sensor networks using elliptic curves cryptography", International Journal of Distributed Sensor Networks,DOI:10.1155/2013/730831, 2013.
. L. Zhou and Z. J. Haas. Securing ad hoc networks. IEEE Network, Vol. 13(6), pp:24.30, 1999.
. S. Hariharan, N. Shroff, and S. Bagchi, "Secure Neighbor Discovery in Wireless Sensor Networks", Technical Report ECE 07-19, Purdue Univ., 2007.
. S. Yi, P. Naldurg, and R.Kravets. "Security-aware adhoc routing for wireless networks", In MobiHOC Poster Session, 2001.
. S. K. Dhurandher, M. S. Obaidat, K. Verma, P. Gupta, and P. Dhurandher, "FACES: Friend-Based Ad Hoc Routing Using Challenges to Establish Security in MANETs Systems", IEEE Systems, Vol. 5, 2011.
. K. Ullah, R. Das, P. Das, A. Roy, "Trusted and secured routing in MANET: An improved approach", International Journal of IEEESymp. on Adv. Computing and Communication, Pp. 297 - 302, 2015.
. Mohammad Hassan, Machine Learning Techniques for Credit Scoring in Financial Institutions , Machine Learning Applications Conference Proceedings, Vol 3 2023.
. S. A. Thorat, P. J. Kulkarni, "Design issues in trust-based routing for MANET", In Proc. of International Conf. on IEEE Computing, Comm. and Networking Tech., 2014.
. T. Jenitha, P. Jayashree, "Distributed Trust Node Selection for Secure Group Communication in MANET", In Proc. of International Conf. on IEEE 4th Advances in Computing and Comm., 2014.
. P. Narula, S. K. Dhurandher, S. Misra, and I. Woungang, "Security in mobile ad-hoc networks using soft encryption and trust based multipath routing", Int. Journal of Science Direct Comp. Comm., Vol. 31, 2008.
. F. Xing, and Wenye Wang, "On the Survivability of Wireless Ad Hoc Networks with Node Misbehaviors and Failures", IEEE Transactions On Dependable And Secure Computing, Vol. 7, No. 3, 2010.
. E. M. Shakshuki, N.Kang, and T. R. Sheltami, "EAACK-A Secure Intrusion-Detection System for MANETs", IEEE Transactions On Industrial Electronics, Vol. 60, No. 3, March 2013.
. Z. Wei, H. Tang, F. Richard Yu, Maoyu Wang, and Peter Mason, "Security Enhancements for Mobile Ad Hoc Networks With Trust Management Using Uncertain Reasoning", IEEE Transactions On Vehicular Technology, Vol. 63, No. 9, 2014.
. T. Shu and M. Krunz, "Privacy-Preserving and Truthful Detection of Packet Dropping Attacks in Wireless Ad Hoc Networks", IEEE Transactions on Mobile Computing, pp. 1536-1233, 2013.
. H. Kozushko,"Intrusion Detection: Host-Based and Network-Based Intrusion Detection Systems", Independent Study, Vol. 11. pp. 1-23, 2003.
. T. Song, "Formal Reasoning about Intrusion Detection Systems", Computer Science.(n.d), p-1-206, 2007.
. N. Marchang, R. Datta, S. K. Das, "A Novel Approach for Efficient Usage of Intrusion Detection System in Mobile Ad Hoc Networks", IEEE Tran. on Vehicular Technology, Vol. 66(2), Pp. 1684 - 1695, 2017.