Towards Automated and Optimized Security Orchestration in Cloud SLA
Main Article Content
Abstract
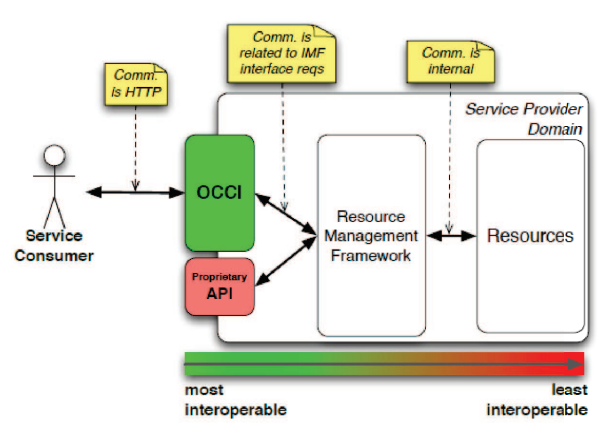
In cloud computing, providers pool their resources and make them available to customers. Next-generation computer scientists are flocking to the cutting-edge field of cloud computing for their research and exploration of uncharted territory. There are still several barriers that cloud service providers must overcome in order to provide cloud services in accordance with service level agreements. Each cloud service provider aspires to achieve maximum performance as per Service Level Agreements (SLAs), and this is especially true when it comes to the delivery of services. A cloud service level agreement (SLA) guarantees that cloud service providers will satisfy the needs of large businesses and offer their clients with a specified list of services. The authors offer a web service level agreement–inspired approach for cloud service agreements. We adopt patterns and antipatterns to symbolize the best and worst practices of OCCI (Open Cloud Computing Interface Standard), REST (Representational State Transfer), and TOSCA (Topology and Orchestration Specification for Cloud Applications) with DevOps solutions, all of which API developers should bear in mind when designing APIs. When using this method, everything pertaining to the cloud service, from creation to deployment to measurement to evaluation to management to termination, may be handled mechanically. When distributing resources to cloud apps, our system takes into account the likelihood of SLA breaches and responds by providing more resources if necessary. We say that for optimal performance, our suggested solution should be used in a private cloud computing setting. As more and more people rely on cloud computing for their day-to-day workloads, there has been a corresponding rise in the need for efficient orchestration and management strategies that foster interoperability.
Article Details
References
Islam, Chadni. (2020). A Multi-Vocal Review of Security Orchestration. 10.1145/3305268".
S., Shilpashree& Patil, Renuka & C, Parvathi. (2018). “Cloud computing an overview”. International Journal of Engineering & Technology. 7. 2743-2746. 10.14419/ijet.v7i4.10904.
Paladi, Nicolae &Michalas, Antonis & Dang, Hai-Van. (2018). Towards Secure Cloud Orchestration for Multi-Cloud Deployments. 1-6. 10.1145/3195870.3195874.
Kalliola, Aapo& Lal, Shankar &Ahola, Kimmo & Oliver, Ian &Miche, Yoan& Aura, Tuomas. (2018). Security Wrapper Orchestration in Cloud. ARES 2018: Proceedings of the 13th International Conference on Availability, Reliability and Security. 1-6. 10.1145/3230833.3232853.
Khan, Imran &Alam, Mahfooz. (2017). Cloud computing: Issues and future direction. Global Sci-Tech. 9. 37. 10.5958/2455-7110.2017.00005.2.
Bajpai, D, Vardhan, M, Gupta, S, Kumar, R, Kushwaha DS 2012, “Security Service Level Agreements Based Authentication and Authorization Model for Accessing Cloud Services”. in Proceedings of the Second International Conference on Advances in Computing and Information Technology (ACITY), Chennai, India, Vol. 1.
Da silva, DA, & De Gues, PL, 2014, “An Approach to Security-SLA in Cloud Computing Environment”, in the proceedings of the IEEE Latin-American Conference on Communications, pp. 1-6.
Guila, P &Sood, S 2013, “Dynamic Ranking and Selection of Cloud Providers Using Service Level Agreements”, in proceedings of the International Journal of Advanced Research in Computer Science and Software Engineering, Vol. 3, no. 6.
Nayak,SK, Mohapatra, S, & Majhi, B 2012, “An Improved Mutual Authentication Framework for Cloud Computing”, International Journal of Computer Applications, vol 52, no, 5, pp. 36-41.
Rady, M 2012, “Parameters for Service Level Agreements Generation in Cloud Computing- A Client-Centric Vision”. ER Workshops 2012, pp. 13-22.