Security Awareness Model for Artificial Intelligence and Internet of Things
Main Article Content
Abstract
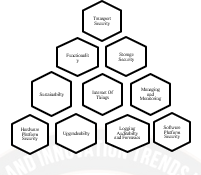
With human engagement replacing artificial intelligence in the provision of services, the position of intelligence systems is rapidly changing. The Internet of Things (IOT) plays a prominent role in these variations as it is a cutting-edge and developing technology that connects physical objects to the virtual world, enabling anytime, everywhere connectivity for anything. A technology known as the Internet of Things (IOT) enables the networked connection and data transfer of physical objects, people, gadgets, cars, and other things. IOT eliminates the need for computer-human contact by speaking directly to the user.This encourages increased communication between entities as a result. It can enhance the fundamental services provided in the industries of transportation, banking, healthcare, and education. Recent analyses have shown that the Internet of Things (IOT) and its related components are very susceptible to security vulnerabilities. Using artificial intelligence approaches, IOT security issues can be rectified (AI). AI develops crucial apps that enable data flow in an IoT environment. Intelligent transmission technique.
Article Details
References
J.Gubbi, R.Buvya, S. Marusic and M. Palaniswami, “Internet of things: A vision, architectural elements, and future directions,” in Elsevier, 2013, pp. 1645-1660.
Kopetz, H. (2011). Internet of things. In Real-time systems (pp. 307-323). Springer US.
Weber, R. H., & Weber, R. (2010). Internet of Things (Vol. 12). New York, NY, USA: Springer.
Wortmann, F., &Flüchter, K. (2015). Internet of things. Business & Information Systems Engineering, 57(3), 221-224.
A. W. Burange and H. D. Misalkar, “Review of inernet of things in development of smart cities with data management and privacy,” in international conference on advances in computer engineering and application, IEEE,2015, pp. 189-195.
K. Zhao and L. Ge, “A survey on the internet of things security,” in IEEE, 2013, pp. 663-667.
C. W. Axlrod, “Enforcing security, safety and privacy for the internet of things,” in systems, applications and technology conference (LISAT), IEEE, 2015.
Sattikar, A. A., & Kulkarni, R. V. A Role of Artificial Intelligence Techniques in Security and Privacy Issues of Social Networking.
Poniszewska-Maranda, A., & Kaczmarek, D. (2015, September). Selected methods of artificial intelligence for Internet of Things conception. InComputer Science and Information Systems (FedCSIS), 2015 Federated Conference on (pp. 1343-1348). IEEE.
Chakrabarti, P. (2009). Information Security: An Artificial Intelligence And Data Mining Based Approach. International Journal of Engineering and Technology, 1(5), 448.
Sumit Kumar, Zahid Raza, “Internet of Things: Possibilities and Challenges”, International Journal of Systems and Service-Oriented Engineering (IJSSOE), IGI Global, pp 32-52 Volume 7, Issues 3, July-September 2017, ISSN 1947-3052, DOI: 10.4018/IJSSOE.2017070103.
Sharma, P., Sharma, N., & Singh, R. (2012). A Secure Intrusion detection system against DDOS attack in Wireless Mobile Ad-hoc Network. International Journal of Computer Applications, 4121, 975–8887. doi:10.5120/5824-8064.
AbdulazizAldaej“Enhancing Cyber Security in Modern Internet of things (IoT) Using Intrusion Prevention Algorithm for IoT (IPAI)” IEEE Access, VOLUME XX, 2017, DOI 10.1109/ACCESS.2019.2893445.
A. V. Dastjerdi and R. Buyya, “Fog Computing: Helping the Internet of Things Realize Its Potential,” IEEE, vol. 49, no. 8, pp. 112–116, Aug. 2016.